New vulnerabilities were discovered in LG TVs that would allow unauthorized access to the devices’ root systems, potentially exposing thousands of devices worldwide.
The discovery, made as part of Bitdefender’s ongoing audit of popular Internet of Things (IoT) hardware, focuses on vulnerabilities within WebOS versions 4 through 7 utilized in LG TVs.
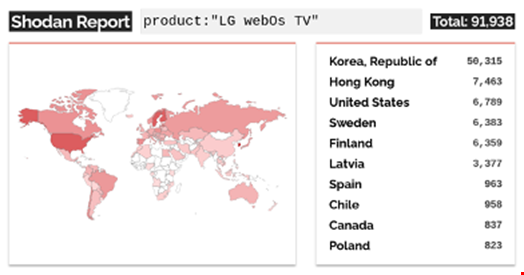
The identified issues permit unauthorized access to the TV’s root system by bypassing the authorization mechanism. Despite being intended for LAN access only, over 91,000 devices exposing this service to the internet have been identified through Shodan, an internet-connected device search engine.
Among the vulnerabilities identified, CVE-2023-6317 stands out, as it allows attackers to bypass authorization mechanisms, granting unauthorized access to the TV’s root system.
Furthemore, CVE-2023-6318 enables attackers to escalate their access to root privileges, exacerbating the security threat. Additionally, CVE-2023-6319 permits the injection of operating system commands, while CVE-2023-6320 facilitates authenticated command injection.
The affected models include LG43UM7000PLA, OLED55CXPUA, OLED48C1PUB and OLED55A23LA. Devices running WebOS versions 4.9.7 to 7.3.1 are confirmed to be affected.
Read more on IoT vulnerabilities: Half of IT Leaders Identify IoT as Security Weak Point
“Attackers could use the compromised Smart TV as a starting point to launch additional attacks against remote systems or hosts,” explained Thomas Richards, principal security consultant at the Synopsys Software Integrity Group.
According to the security expert, if attackers manage to gain administrative access to the TV, the user’s private information, including login credentials, could also be compromised.
“Smart TV owners should not have their TVs directly connected to the internet. Keeping the TV behind a router will reduce the likelihood of a compromise since remote attackers will not be able to reach it,” Richards added. “Enabling the automatic update option on the TV will keep the TV up to date with vendor patches to remediate security risks.”
Bitdefender’s disclosure timeline revealed the approach taken, with vendor notification occurring on November 1 2023, preceding a patch release on March 22 2024 by several months.
Prompt patching and updates are imperative to mitigate potential risks, safeguard user privacy and enhance device security in the face of evolving threats.
Image credit: monticello / Shutterstock.com
