Cloud-based cyber-attacks saw a marked increase in 2024, with threat actors adopting new tactics to exploit cloud resources at an unprecedented scale, according to Sysdig Threat Research Team’s (TRT) latest report.
Beyond LLMjacking, which was observed by the firm to target large language models (LLMs), attackers in 2024 weaponized open-source tools and escalated their use of automation, causing financial damage and increasing the attack surface for cloud-hosted enterprises.
“The stolen enterprise access in the first LLMjacking attack was a local Anthropic Claude 2. x model that could cost victims up to $46,000 per day in consumption costs. These daily costs for the newer Claude 3.5 Opus version could double or triple the daily cost,” Sysdig explained.
Weaponized Open-Source Tools Increase Cloud Attack Scale
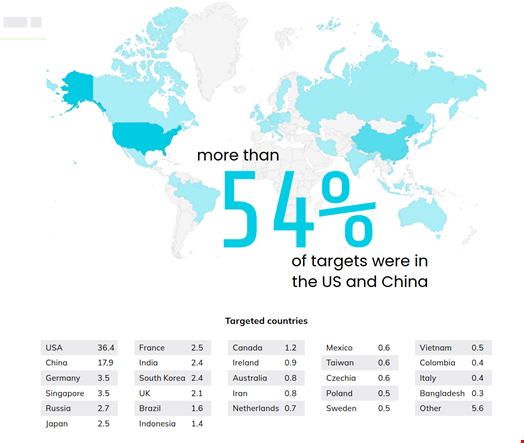
Notable among the new attacks is the use of SSH-Snake, an open-source tool originally developed for penetration testing. The Crystalray threat group used this tool to steal over 1,500 unique credentials in just five months, targeting the US, China and other regions.
Crystalray victims, many of them cloud service users, faced severe security breaches and credential loss, further compounded by the growing number of cloud vulnerabilities.
Read more on these attacks: Crystalray Cyber-Attacks Grow Tenfold Using OSS Tools
Weaponized open-source tools were a key trend in 2024. Sysdig said Crystalray's use of SSH-Snake underscores how quickly attackers are able to exploit new tools to expand the scale of their campaigns.
Attackers used these tools to access expensive cloud resources, sell stolen credentials and conduct resource-jacking campaigns. A single CRYSTALRAY victim’s credentials could sell for $20, but the broader impact on their cloud environments and financial security often stretched much further.
Botnets Drive Stealthy, Profitable Cloud Exploitation
Botnets have also played a significant role in the cloud attack landscape in 2024 so far. Rubycarp, a stealthy botnet, remained undetected for over a decade before Sysdig’s discovery.
This financially motivated group customized its tools regularly, making detection difficult and evading security measures by attacking multiple vulnerabilities in cloud infrastructure. RUBYCARP members were able to mine cryptocurrencies using compromised cloud accounts, amassing significant profits while maintaining low visibility.
Sysdig warned that these evolving threats highlight the scalability and automation of cloud-based attacks. In some cases, attacks unfolded within minutes.
“Within minutes of obtaining access to the victim’s environment, the attacker attempted to create 6,000 nodes using the compromised cloud account. This process was automated, taking approximately 20 seconds to launch each batch of 500 micro‑sized EC2 instances per region. With micro‑sized nodes, 6,000 could cost the victim $2,000 per day, but with public IP addresses, that goes up to $22,000.”
Because of these threats, Sysdig’s report emphasized the need for real-time threat detection and a proactive approach to monitoring cloud environments. Understanding usage patterns and responding quickly to abnormal activity are critical in curbing the rising wave of cloud exploitation.
