The LockBit ransomware gang was found to be the most active in terms of total number of victims from January to May 2023 and has developed encryptors that specifically target Macs.
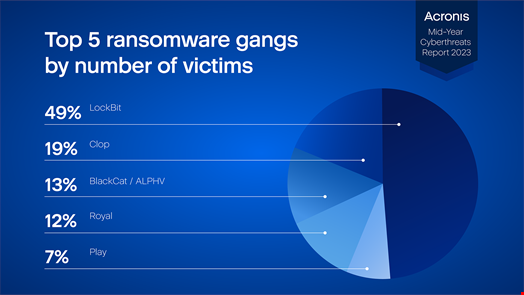
According to analysis in the Acronis Mid-Year Cyberthreats Report 2023 LockBit’s known victims totaled 280 (49% of the total reviewed) and included the Housing Authority of the City of Los Angeles (HACLA), Aguas do Porto and Wabtec Corporation.
Clop followed with 106 victims (19%), BalckCat/ALPHV with 74 (13%), Royal with 68 (12%) and Play with 43 (7%).
Read more: Royal Mail’s Attackers Linked to Russia-Backed LockBit
In its analysis Acronis noted that the LockBit gang has created encryptors targeting Macs for the first time, becoming one of the first major ransomware operations to specifically target macOS.
“As Macs are widely used in some countries, especially the US, we can expect devastating ransomware attacks in the future — an unwelcome surprise for the many Mac users who still believe they are effectively immune against malware,” the report notes.
The report also notes that ransomware variants are falling but businesses continue to lose data and money.
“Ransomware gangs are still breaching companies around the globe fairly easily, and continue to make malicious use of popular legitimate tools after breaching systems,” says the report.
Email Attacks
The report also found that the number of email attacks seen in 2023 has surged by a staggering 464% compared to the first half of 2022.
In Q1 2023, 30.3% of all received emails were spam and 1.3% contained malware or phishing links. It is clear that phishing continues to be one of the preferred tools used by cyber criminals today.
Acronis has also observed a new phishing campaign that targets US taxpayers by impersonating W-9 tax forms allegedly sent by the Internal Revenue Service and companies you work with. This campaign spreads Emotet.
Another new phishing campaign observed has been targeting users of the cryptocurrency hardware wallet firm Trezor.
In summary of email phishing threats Acronis highlighted the importance of anti-phishing defenses and strong authentication, as well as an overall multilayered approach to cybersecurity.
“If phishing threats aren’t blocked right away, it’s important to have other detection technologies that can stop the malware later in its cycle,” the report notes.
Cyber Criminals Using AI
It is well reported that cyber criminals are becoming more sophisticated in their attacks, using AI and existing ransomware code to drill deeper into victims’ systems and extract sensitive information.
The report notes that there have already been phishing emails in the wild that were created by AI.
“In classic CEO fraud or business email compromise (BEC) scams, the AI can even respond to potential questions, greatly reducing the attacker’s effort,” the report says.
AI-created malware is adept at avoiding detection in traditional antivirus models and public ransomware cases have exploded relative to last year, Acronis noted.
Read more: ChatGPT Creates Polymorphic Malware
Despite AI making malware generation easier for attackers, Acronis notes that the malware created is “not very sophisticated.”
“It is therefore unlikely that the big APT groups will jump on this bandwagon anytime soon. Of course, the models will continue to improve in the future,” the report says.
