Read more about Lumma Stealer:
- Infostealer Lumma Evolves With New Anti-Sandbox Method
- Famous YouTube Channels Hacked to Distribute Infostealers
- LummaC2 Infostealer Resurfaces With Obfuscated PowerShell Tactics
Instant messaging app Telegram is gaining traction as a malware-spreading platform, according to cybersecurity firm McAfee.
Two McAfee researchers analyzed in a November 20 blog post how Lumma Stealer, one of the most used infostealers, is being distributed on Telegram.
The researchers believe that threat actors have identified the messaging platform as a lucrative distribution vector because it reaches a broad and often unsuspecting audience.
Deploying the infostealer via Telegram also bypasses traditional detection mechanisms.
Lumma Stealer Disguised as Benign Apps
The McAfee researchers identified two prominent Telegram channels distributing Lumma Stealer payloads through cracking software or archived versions of seemingly benign software.
The first channel, named VIP HitMaster Program, has over 42,000 subscribers, and the second, named MegaProgram +, has 8660. Both channels regularly forward each other’s messages.
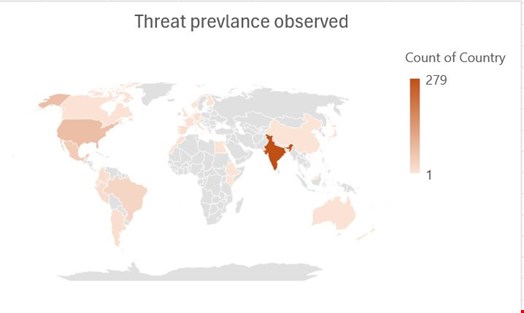
Indian Telegram users are the most affected by this threat, followed by US and European users.
Analysis: Fake CCleaner Archive File
In one case analyzed by the researcher, a file appeared as CCleaner 2024, a system cleaner and performance optimizing application, but ultimately distributed Lumma Stealer.
Although the file appeared as a CCleaner executable file – ‘CCleaner.exe’ – once the .rar file was extracted, it actually included two payloads, one being a .NET file “XTb9DOBjB3.exe”(Lumma_stealer).
Connection to Steam for Command and Control
The file also contained several encryption and obfuscation features.
For instance, it hid code that connected to a Steam account name, with the user’s name obfuscated and linked to several aliases.
Then, it decoded the name to uncover the attacker's command and control (C2) server address. This allowed the malware to connect the infected device to the attacker’s server, enabling activities like stealing data or downloading more malicious files.
By doing this, the attackers make it harder for security systems to spot and block the connection.
“Infostealers’ spread through Telegram channels demonstrates how easily threat actors can exploit popular platforms to distribute malicious code to a broad audience. With Lumma Stealer capable of stealing sensitive information and compromising user privacy, the potential damage it can cause is significant,” the McAfee researchers concluded.
Read now: Top 10 Infrastructure Elements of Ransomware-as-a-Service
