Advanced email attacks, including phishing and business email compromise (BEC), are surging in the manufacturing sector as cybercriminals target an industry with a low tolerance for downtime.
Phishing attacks in the sector have surged 83% in the past 12 months, with Generative AI technologies enabling threat actors create greater volumes of sophisticated email attacks.
Mike Britton, CIO at Abnormal Security, told Infosecurity that the spike in phishing activity is partly due to generative AI tools ensuring these messages lack the characteristics most commonly associated with phishing emails, such as poor spelling and grammar.
“Now, even inexperienced petty criminals can leverage widely accessible tools like ChatGPT to craft perfectly written, personalized, and seemingly realistic emails, making them exponentially more difficult for employees to identify,” he explained.
Britton added that attackers are now able to use AI to scale and layer in additional specificity and customization into phishing emails at ease, making such attempts “nearly impossible” for legacy email controls, such as secure email gateways, to stop.
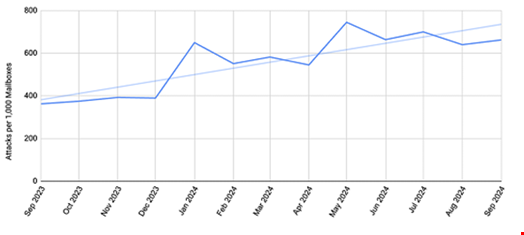
Manufacturing Especially Vulnerable to BEC and VEC Attacks
The study by Abnormal Security also found that business email compromise (BEC) attacks targeting manufacturing firms increased by 56% from September 2023 to September 2024.
BEC attacks see threat actors masquerade as trusted parties, such as a senior manager within an organization, often by compromising a legitimate account or using a spoofed email address.
These attacks involve significant research and monitoring of the individual and organization’s communication patterns.
The researchers said that manufacturing firms are particularly susceptible to BEC attacks due to a low tolerance for downtime in the sector. This means employees more likely to fulfill requests quickly.
Read now: Manufacturing Firm Loses $60m in BEC Scam
Additionally, vendor email compromise (VEC) attacks targeting manufacturing rose by 24% over the same period.
These attacks differ from BEC as the threat actors poses as an external third party to dupe their victim into paying phony invoices, updating bank details for future transactions or initiating fraudulent wire transfers.
Abnormal Security said that VEC attacks can be especially difficult to spot as vendor-client relationships are inherently financial and often managed via email, so requests asking for payment or requesting updates to bank account information may not raise any initial red flags.
Manufacturing firms tend to have complicated supply chains that involve numerous smaller vendors and suppliers.
“Unfortunately, many of these smaller suppliers often don't run the same level of security as larger organizations. This leads to attackers being able to compromise, spoof, or otherwise leverage the implicit trust that companies have in their supply chain,” said Britton.
