Microsoft has observed a proliferation of adversary-in-the-middle (AiTM) techniques deployed through phishing-as-a-service (PhaaS) platforms, the company explained in a series of tweets posted on August 28, 2023.
On the one hand, there has been an increasing number of new AiTM-capable PhaaS platforms throughout 2023; on the other, established phishing services, such as PerSwaysion, have also added AiTM capabilities.
The two techniques most commonly used for phishing-powered AiTM attacks are reverse proxy servers and synchronous relay servers.
In the first case, observed in phishing kits like EvilGinx, Modlishka, Muraena, and EvilProxy, every HTTP packet is proxied to and from the original website, making the URL the only visible difference between the phishing page and the legitimate site.
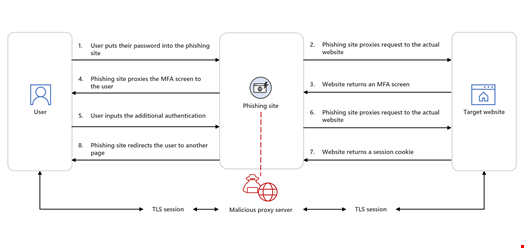
In the second, typically used by Storm-1295, the actor group behind the Greatness PhaaS platform, the target is presented with a copy or mimic of a sign-in page, like traditional phishing attacks.
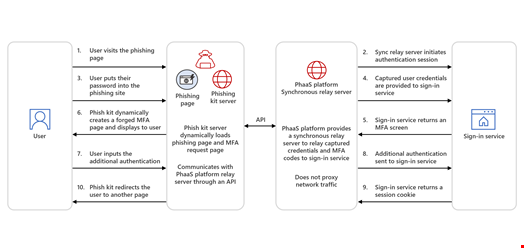
Unlike traditional phishing attacks, AiTM phishing aims to steal session cookies stored by browsers to allow users access to privileged systems without reauthentication. This enables attackers to conduct high-volume phishing campaigns that attempt to circumvent multi-factor authentication (MFA) protections at scale.
This means that incident response procedures for AiTM require the revocation of stolen session cookies.
“This emphasizes the importance of MFA through methods like Microsoft Authenticator, FIDO2 security keys and certificate-based authentication in securing identities,” the company said.
