Eight Microsoft applications for macOS are vulnerable to library injection attacks, potentially allowing adversaries to steal app permissions and breach sensitive data, according to new research by Cisco Talos.
The impacted Microsoft apps include popular services like Microsoft Teams, Outlook, PowerPoint and Word, with eight CVE numbers assigned.
- Microsoft Outlook: CVE-2024-42220
- Microsoft Teams (work or school): CVE-2024-42004
- Microsoft PowerPoint: CVE-2024-39804
- Microsoft OneNote: CVE-2024-41159
- Microsoft Excel: CVE-2024-43106
- Microsoft Word: CVE-2024-41165
- Microsoft Teams (work or school) WebView.app helper app: CVE-2024-41145
- Microsoft Teams (work or school) com.microsoft.teams2.modulehost.app: CVE-2024-41138
Attackers could bypass macOS’ permission model by using existing app permissions without prompting the user for any additional verification.
This could allow attackers to undertake activities such as sending emails from the user account without the user realizing, recording audio clips, taking pictures or recording videos without any user interaction.
macOS’ Permission Model Under Scrutiny
Cisco Talos highlighted macOS’ consent-based permission model, which contains capabilities designed to protect users’ privacy and maintain system security.
However, the operating system trusts applications to “self-police” their permissions, failure to do so could allow attackers to hijack elevated permissions given to the app.
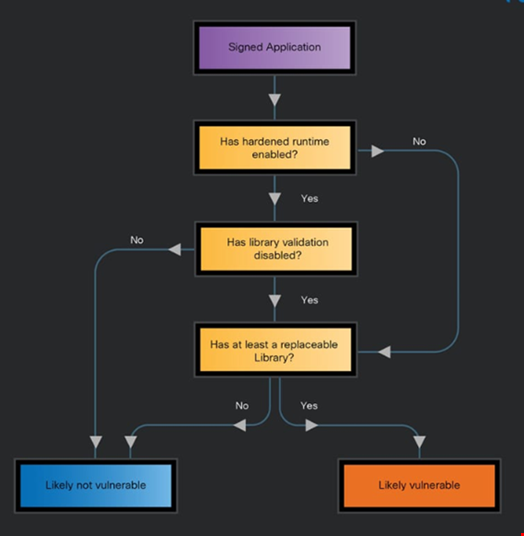
The researchers discovered that the eight Microsoft macOS apps have the ‘com.apple.security.cs.disable-library-validation’ entitlement active.
According to Apple, this entitlement allows the loading of plug-ins signed by third-party developers.
However, this could allow attackers to inject any library and run arbitrary code within the compromised application, potentially leading to the exploitation of the app’s full set of permissions and entitlements.
The presence of the entitlement effectively disables the hardened runtime security feature that is used on the apps.
All the Microsoft Office apps on macOS permit the loading of unsigned dynamic libraries, the researchers observed.
To modify an application that is already executed once, a specific entitlement is required. However, it is possible circumvent this requirement by copying and modifying the application in another folder, such as /tmp.
“Given that there are some relative imports and the entitlement to disable library validation is present, all the Microsoft Office apps are vulnerable to library injection attacks,” the researchers noted.
Microsoft Users Exposed to “Unnecessary Risks”
Cisco Talos researchers said its findings raise questions about the necessity of disabling library validation, especially if no additional libraries are expected to be loaded.
“By using this entitlement, Microsoft is circumventing the safeguards offered by the hardened runtime, potentially exposing its users to unnecessary risks,” they wrote.
After reporting, Microsoft said it considered the uncovered issues to be low risk. However, the tech giant has updated four of the apps so they no longer possess the com.apple.security.cs.disable-library-validation entitlement, meaning they are no longer vulnerable to the described library injection attacks.
The four apps are Microsoft Teams’ main app, WebView app and ModuleHost app, and Microsoft OneNote.
However, Microsoft Excel, Outlook, PowerPoint and Word all remain vulnerable as of August 19, 2024.
The researchers also suggested that macOS could introduce a user prompt to mitigate this risk. This would allow users to decide whether to load a specific third-party plug-in, thereby providing a more controlled means of granting access.
Image credit: Koshiro K / Shutterstock.com
