An unknown threat actor is deploying a large-scale, sophisticated cryptojacking campaign through a series of malicious extensions in Visual Studio Code, Microsoft’s lightweight source-code editor, according to a group of security researchers.
In a new report shared exclusively with Infosecurity, researchers from newly founded cybersecurity startup ExtensionTotal observed that at least nine extensions recently uploaded in the VS Code marketplace were malicious.
These extensions were all published after April 4 by three different authors, mainly one known as ‘Mark H.’ Over 300,000 installations were observed in just three days. The most popular, ‘Discord Rich Presence,’ gained 189,000 installs alone.
According to Itay Kruk, ExtensionTotal co-founder and a former product manager at Zscaler, the extensions are fake VS Code extensions and all nine are part of the same malicious campaign, serving as initial access vectors in a sophisticated multi-stage cryptomining campaign.
Speaking to Infosecurity, a Microsoft spokesperson said the extensions were removed and the publisher was blocked from the Visual Studio Code marketplace. "There’s no action needed from users," they added.
A Sophisticated Cryptojacking Campaign
Seven of the malicious extensions had been uploaded by ‘Mark H,’ including:
- Discord Rich Presence for VS Code
- Claude AI
- Golang Compiler
- Rust Compiler for VSCode
- ChatGPT Agent for VSCode
- HTNL Obfuscator for VSCode
- Python Obfuscator for VSCode
Another, ‘Rojo - Roblox Studio Sync,’ was uploaded by ‘evaera’ and had been downloaded 117,000 times.
The final one, ‘Solidity Compiler,’ published by VSCode Developer, had gained 1300 installs.
“Reaching these numbers in an unusually short period of time strongly suggests that the install counts were artificially inflated, likely in an attempt to establish credibility and reduce user suspicion by making the extensions appear widely trusted and actively used,” wrote Yuval Ronen, Security Researcher at ExtensionTotal and author of the report.
Kruk said that the artificially inflated install counts highlight a concerning vulnerability in the extension ecosystem's trust metrics that attackers are actively exploiting.
Once installed, all nine extensions secretly downloaded and executed a PowerShell script that disabled Windows security, established persistence through scheduled tasks and installed an XMRig cryptominer from a remote command-and-control (C2) server.
XMRig is a popular, open-source cryptocurrency mining software used to mine Monero (XMR) and other cryptocurrencies that use the RandomX or Cryptonight algorithms.
XMRig’s ease of use has made it a popular tool among malicious actors for cryptojacking – secretly mining cryptocurrency on compromised devices without the owner's knowledge or consent.
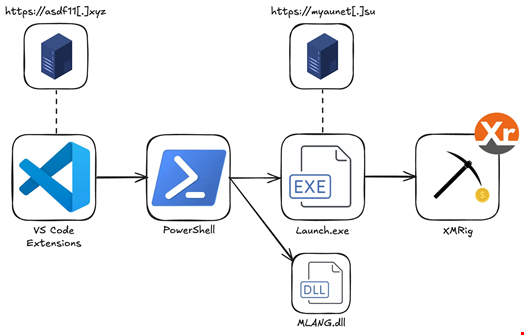
“The attackers created a sophisticated multi-stage attack, even installing the legitimate extensions they impersonated to avoid raising suspicion while mining cryptocurrency in the background,” Kruk told Infosecurity.
He added that each extension contained the exact same malicious code, communicated with the same C2 server and downloaded the same malicious payload, suggesting that they originated from the same source.
The C2 domain ‘asdf11[.]xyz’ was created on April 4, the same day the first extensions were published.
While Kruk admitted that his team regularly detects malicious extensions in the VSCode marketplace, he added that this scheme was “much more sophisticated and impactful than usual, notably in the sophistication of the techniques used.”
The ExtensionTotal researchers have reported the malicious extensions to Microsoft and published their findings in a blog post.
Users can report suspicious extensions from the extension’s details page on the VS Marketplace website, using the 'Report a concern' button or by emailing 'vsmarketplace@microsoft.com' directly.
This article was updated on April 8 to add Microsoft's response.
Read now: Security Researcher Proves GenAI Tools Can Develop Google Chrome Infostealers
