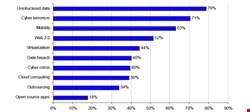
The CA-sponsored Cyber Security Mega Trends: US Federal Government report, released late last week, found that almost eight in every 10 respondents thought that collaboration tools increased the storage of unstructured data sources with potentially sensitive information. 52% said that web 2.0 applications also made organizations more susceptible to attacks and data loss. And 63% of people said that employee mobility within the government contributed significantly to endpoint information security risks.
35% of the 217 valid respondents said that their networks had been hacked at least once in the past year. Even more worrying was the other 38%, who were unsure about unauthorized intrusions [although, this is perhaps the most honest response, given that many networks may have been hacked without the owners' knowledge].
The report closely mirrors results from the CDW Government survey of 300 federal IT professionals released just a week earlier, in which 60% of respondents said that information security threats related to mobile computing have increased over the last year.
In spite of these heightened concerns around information security, only 52% of all organisations took the appropriate steps to comply with privacy and security requirements (including FISMA), according to the Ponemon Institute report. This is the exact percentage of respondents to the CDW Government survey that said they didn't have sufficient information security budget.
Recommendations from the report, based on interview results, included creating and enforcing policies that restrict access to data and IT assets to authorized parties only. Securing corporate endpoints was also high on the list, as was ensuring that third parties with access to sensitive data take appropriate information security precautions.