Nation-state threat actors have ramped up cooperation with cybercriminals in the past year to advance their political and military goals, according to Microsoft’s Digital Defense Report 2024.
The use of cybercriminals by nation-states has served a variety of purposes, including to collect intelligence, conduct operations for financial gain, and to make use of tools favored by these financially-motivated groups, such as infostealers and command and control frameworks.
Examples of this collaboration include:
- Russia appears to have outsourced some of its cyberespionage operations to criminal groups, especially operations targeting Ukraine. This includes cybercriminal group Storm-2049 using Xworm and Remcos RAT – commodity malware associated with criminal activity – to compromise at least 50 Ukrainian military devices in June 2024
- Iranian nation state actors used ransomware attacks for financial gain from some of their offensive cyber operations. For example, a cyber-enabled influence operation run by an Islamic Revolutionary Guard Corps (IRGC) group tracked as Cotton Sandstorm marketed stolen Israeli dating website data through two of its cyber personas between September 2023 and February 2024
- North Korea appears to be conducting ransomware operations for both intelligence gathering and monetization of its access. Moonstone Sleet, a new North Korean actor identified in May 2024, developed a custom ransomware variant called FakePenny which it deployed at organizations in aerospace and defense after exfiltrating data from the impacted networks
This coordination between financially motivated cybercrime and state-sponsored activity has also enabled cybercriminal groups to access and learn new tools and techniques, the tech giant said.
The report highlighted trends observed in the period July 2023 to June 2024.
Nation-State Activity Heavily Concentrated
The report found that nation-state cyber activity has been concentrated around sites of active military conflict or regional tension.
Microsoft observed that 75% of Russian nation-state attacks targeted Ukraine or a NATO member state.
The focus of these attacks were European and North American government agencies and think tanks, likely for intelligence collection related to the war in Ukraine.
China’s geographic targeting remained similar to the last few years, with North America, Taiwan and other countries in Southeast Asia making up 72% of its cyber activity targets.
China-based cyber actors Raspberry Typhoon, Flax Typhoon and Granite Typhoon have intensively targeted entities associated with IT, military, and government interests around the South China Sea.
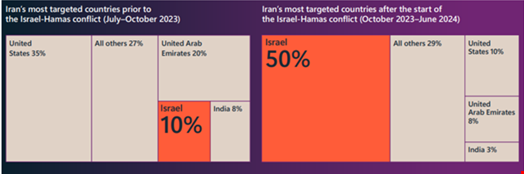
Iran has placed a significant focus on Israel in the past year, making up 50% of its activity from October 2023 to June 2024, following the outbreak of the Israel-Hamas conflict.
Iranian actors continued to target the US and Gulf countries, including the UAE and Bahrain, in part because of their normalization of ties with Israel and Tehran’s perception that they are both enabling Israel’s war efforts, Microsoft reported.
Russia, Iran and China’s Interference with US Election
Microsoft highlighted Russia, Iran and China’s influence operations relating to the upcoming US election.
Each of the nations used ongoing geopolitical matters to drive discord on sensitive domestic issues leading up to the November Presidential election, seeking to sway audiences in the US to one party or candidate over another, or to degrade confidence in elections as a foundation of democracy.
For example, Russian influence actor Ruza Flood has developed US election-themed websites, using names like “50 States of Lies” and “Election Watch,” which spread anti-Ukraine, anti-US propaganda across social media platforms.
Iran has sought to influence the US election in two main ways: conducting cyber intrusions into political accounts potentially for hack-and-leaks and launching a stream of polarizing content on covert news sites.
Iran Behind Trump Campaign Hack, US Government Confirms
China has not been as active as Russia and Iran in interfering in US elections, but has been observed using covert social media networks to sow discord among the US public.
For example, in late April 2024, Chinese nation state-linked influence actor Taizi Flood launched an influence campaign leveraging the surge of Israel-Palestine-related protests on US college campuses.
Microsoft expects US election influence activity to accelerate over the next two weeks ahead of voting day.
Ransomware Attacks Rise
There was a 2.75 increase year-over-year in ransomware attacks targeting Microsoft customers.
The top five ransomware groups accounted for 51% of these attacks. These were Akira (17%), LockBit (15%), Play (7%), BlackCat (6%) and Basta (6%).
The most prevalent initial access techniques for ransomware deployment continue to be social engineering, such as email phishing and voice phishing.
Threat actors also took advantage of newly identified common vulnerabilities and exposures (CVE) with Common Vulnerability Scoring System (CVSS) scores above 8 to launch ransomware attacks.
In more than 90% of cases where attacks progressed to ransom stage, the attacker leveraged unmanaged devices in the network, either to gain initial access or to remotely encrypt assets at the impact stage, the report found.
However, there was a threefold decrease in ransom attacks reaching the encryption stage. Microsoft said Automatic attack disruption contributed to this positive trend in decreasing successful attacks.
Another possible factor in this decrease is the trend of ransomware attackers prioritizing data exfiltration over encryption to extort victims.
