Over 60% of vulnerabilities discovered in network and security appliances in 2023 were exploited as zero days, according to a new Rapid7 report.
This follows a broader trend of attackers being adept at exploiting vulnerabilities before a patch has been released. The researchers found that more mass compromise events arose from zero-day vulnerabilities than from n-day vulnerabilities in 2023 (53% vs 47%).
Last year’s numbers represent a return to 2021 levels of widespread zero-day exploitation (52%), following a slight respite (43%) in 2022.
Caitlin Condon, Director of Vulnerability Intelligence at Rapid7, commented: “Our data shows 2021 to have been the dividing line between a ‘then’ and a ‘now’ in zero-day attacks. Since that time, the median number of days between vulnerability disclosure and exploitation, which we began tracking several years ago, has stayed in single digits across the CVEs in our annual datasets; widespread exploitation of major vulnerabilities has shifted from a notable event to a baseline expectation.”
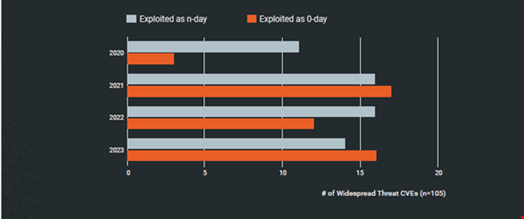
Mass compromise events occur when vulnerabilities are exploited to compromise many organizations across many verticals and geolocations.
Attacks Better Planned and Orchestrated
The report found that as in previous years, zero-day attacks and widespread exploitation remained common across the vulnerabilities discovered in 2023.
However, there has been a “pronounced shift” in the way many of these mass compromise events are carried out since the start of 2023. Nearly a quarter (23%) of widespread threat common vulnerabilities and exposures (CVEs) from highly orchestrated zero-day attacks, in which often hundreds of organizations were compromised by a single attacker.
Prior to 2023, Rapid7 said the most common attack pattern for widespread compromise events was an initial wave of low-skilled exploit attempts followed by more adept ransomware group and/or APT exploitation – an approach dubbed “many attackers, many targets.”
Among the mass compromise events where initial exploitation was orchestrated and executed by a single motivated threat actor since the start of 2023 were:
- The Clop ransomware gangs targeting of MOVEit and GoAnywhere MFT file transfer solutions via new zero-day exploits. These well-planned attacks resulted in data exfiltration and extortion for hundreds of organizations around the world.
- A single threat actor used a zero-day command injection exploit to compromise a large number of Barracuda Networks’ Email Security Gateway (ESG) appliances.
- A suspected Chinese APT campaign targeting zero-day vulnerabilities in Ivanti products, resulting in vulnerable devices being exploited en-mass.
Condon said: “This is a mature, well-organized cybercrime ecosystem at work, with increasingly sophisticated mechanisms to gain access, establish persistence, and evade detection.
“The data is telling us that we are experiencing the intensification of a multi-year trend; now more than ever, implementing zero-day patching procedures for critical technologies is key.”
Over a third (36%) of widely exploited vulnerabilities have occurred in network perimeter technologies since the start of 2023, nearly doubling from the previous year.
The researchers also observed that most of the widely exploited CVEs from the past few years have arisen from easily exploitable root causes, like command injection and improper authentication issues, shifting away from memory corruption exploits.
Additionally, 41% of incidents observed by Rapid7 in 2023 were the result of missing or unenforced multi-factor authentication (MFA) on internet facing systems, particularly VPNs and virtual desktop infrastructure.
Regressive Practices Among Software Vendors
The researchers said that the evolving nature of mass compromise vulnerability exploits has induced “regressive practices” among software developers.
This includes a growing trend of vendors silently withholding advisories and CVE descriptions until days or weeks later. Even when this information is published, many appear to be deliberately obfuscating vulnerability details, such as root cause and attack vector information. This is likely due to a mistaken belief that this obscurity deters adversaries and mitigates reputational risk, said Rapid7.
Additionally, the broader security marketed is starting to veer more heavily towards sharing vulnerability and exploit information in closed loops rather than openly.
This issue has been exacerbated by industry concern over the future of the National Vulnerability Database (NVD), the researchers added.
