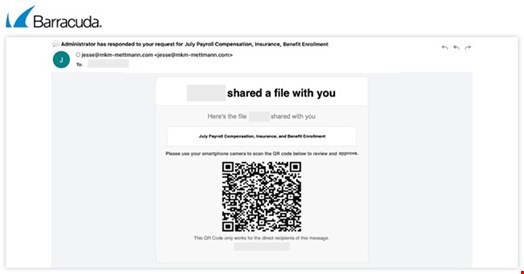
A new generation of QR code phishing (quishing) attacks have been uncovered by threat analyists at Barracuda.
Research by the email protection firm highlighted new techniques that have been designed to evade traditional security defenses by including QR codes built from text-based ASCII/Unicode characters rather than the standard static image.
This tactic is designed to evade optical character recognition (OCR)-based defenses. In an email, it will look like a traditional QR code. To a typical OCR detection system, it appears meaningless.
Another technique sees the use of binary large object universal resource identifiers (URIs) to create hard-to-detect phishing pages.
Blob URIs allow web developers to work with binary data like images, videos or files directly within the browser, without having to send or retrieve it from an external server, Barracuda explained in a blog.
Because Blob URIs don’t load data from external URLs, traditional URL filtering and scanning tools may not initially recognize the content as malicious.
Blob URIs can also be difficult to track and analyze because they are created dynamically and can expire quickly.
The threat analysts have not seen any examples of the two techniques used at the same time.
“In traditional QR code attacks, the threat actors embed malicious links into the QR code. Security tools scan the image for known malicious links and block them,” explained Ashitosh Deshnur, Threat Analyst, Barracuda. “The new generation of QR code phishing techniques try to get around this by either making it impossible for image-based security scanning tools to read the QR code, or by making it harder for detection systems to identify and block malicious content.”
In 2023, Barracuda research showed that around 1 in 20 mailboxes were targeted with QR code attacks in the last quarter of the year.
