A North Korean-backed hacking group has engaged in a ransomware campaign for the first time, according to Palo Alto Networks.
Jumpy Pisces, a hacking group tied to the Reconnaissance General Bureau of the Korean People's Army, has been involved in a recent ransomware incident, according to a new report by Palo Alto’s threat intelligence team, Unit 42, published on October 30.
This marks a shift in the nation-state group’s tactics and the first time they have been involved with financially motivated cyber threat actors.
Jumpy Pisces and Play Collaboration
In early September 2024, Unit 42 engaged in incident response services for a client impacted by Play ransomware.
First detected in 2022, Play is now one of the most active ransomware gangs. Palo Alto tracks this group as Fiddling Scorpius.
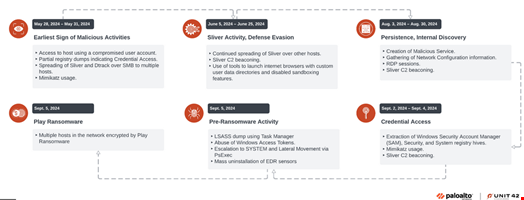
Upon investigation, Unit 42 observed the earliest signs of unauthorized activity at the end of May 2024. The researchers assessed with high confidence that it came from Jumpy Pisces, with the group gaining initial access via a compromised user account.
The North Korean group carried out lateral movement and maintained persistence by spreading the open-source tool Sliver and their unique custom malware, DTrack, to other hosts via Server Message Block (SMB) protocol.
These tools continued communicating with Jumpy Pisces’ command-and-control (C2) server until early September. This ultimately led to the deployment of Play ransomware.
“It remains unclear whether Jumpy Pisces has officially become an affiliate for Play ransomware or if they acted as an initial access broker (IAB) by selling network access to Play ransomware actors,” Unit 42 researchers wrote.
However, Play claimed in its data leak site (DLS) that it does not operate a ransomware-as-a-service (RaaS) model, suggesting that the IAB hypothesis is more likely.
“Either way, this incident is significant because it marks the first recorded collaboration between Jumpy Pisces […] and an underground ransomware network,” Unit 42 researchers wrote. “This development could indicate a future trend where North Korean threat groups will increasingly participate in broader ransomware campaigns, potentially leading to more widespread and damaging attacks globally.”
Intrusion Tactics and Tools
Jumpy Pisces gained unauthorized initial access after a compromised user account accessed a particular host through a firewall. Partial registry dumps on the host indicate possible use of Impacket's credential harvesting module, secretsdump.py.
Attackers copied files associated with the Sliver and DTrack malware family to various hosts using the compromised account over SMB.
DTrack was blocked by the target’s endpoint detection and response (EDR) solution. However, Unit 42 observed Sliver beaconing activity spanning multiple days until early September 2024, with quiet periods in July and sporadically on other days.
An unidentified threat actor entered the network in early September through the same compromised user account. They carried out pre-ransomware activities, including credential harvesting, privilege escalation and the uninstallation of EDR sensors, eventually leading to the deployment of Play ransomware.
Alongside Sliver and DTrack, attackers used a dedicated tool built to create a privileged user account on victim machines with Remote Desktop Protocol (RDP) enabled, a customized version of Mimikatz, a publicly available credential dumping tool and a trojanized binary that steals browser history, autofills and credit card details for Chrome, Edge and Brave internet browsers.
All these tools were signed using several invalid certificates previously linked to Jumpy Pisces.
