NullBulge is a new threat actor emerged in Spring 2024, targeting AI-centric applications and games.
The group claimed on July 12 to have stolen and leaked over a terabyte of data from Disney’s internal Slack channels.
In a new report, cybersecurity provider SentinelOne shared some of the techniques, tactics, and procedures (TTPs) of this so-called ‘hacktivist’ group.
NullBulge’s Emergence: Hacktivists Seeking Financial Gain
According to SentinelLabs, SentinelOne’s threat intelligence service, NullBulge, appeared between April and June 2024.
It maintains a public-facing presence on social media platforms like X and 4chan, where it claims to be a hacktivist group “protecting artists around the world” against AI. It also claims to be uninterested in profit, although SentinelOne observed malicious activities that may indicate otherwise.
However, Ilia Kolochenko, CEO at ImmuniWeb, believes the Disney hack it is more likely to be a financially motivated attack than an act of hacktivism.
“Hacktivists are highly unlikely to run operations of such scale to protect intellectual property and the rights of artists,” he said.
Given the volume and nature of the reportedly compromised data, it may rather be exploited to blackmail Disney, similar to the notoriously devastating Sony hack.
He added that another plausible motivation for the attack could be censoring certain movies, topics or ideas from Disney’s digital content, suggesting a politically rather than morally driven act.
Data Leak Sites Active
NullBulge has multiple active data leak sites (DLS). The first two, nullbulge[.]com and nullbulge[.]onion, went live in late May 2024.
As of July 2024, the nullbulge[.]se and nullbulge[.]co domains are active and updated on an ongoing basis.
The group also has a history of selling infostealer logs from their custom stealer and stolen OpenAI API keys on the cracked[.]io underground forum, suggesting that protecting artists’ rights is not their sole motivation.
There has been some reporting that the group claims to be of Russian origin. However, this has been disputed by Rafe Pilling, director of threat intelligence at Secureworks.
“We have no evidence of their claim of being Russian,” he said. “We usually see these groups focused on crime for financial gain. The language on the X feed feels more like an English speaker. One reason they may be making this claim is to give the impression that they are outside of Western law enforcement jurisdiction.”
SentinelLabs researchers noted that NullBulge demonstrates a shift in the ransomware ecosystem where actors adopt hacktivist causes for financial gain.
AI Supply Chain Attacks on GitHub and Hugging Face
In May and June 2024, NullBulge carried out a series of malicious campaigns targeting the supply chain of AI tools and platforms.
Its first targets were users in AI-centric applications and gaming communities.
For these campaigns, NullBulge typically follows a ‘poisoning the well’ approach.
This means that the group targets the software supply chain by weaponizing code in publicly available repositories on GitHub and Hugging Face, leading victims to import malicious libraries, or through mod packs used by gaming and modeling software.
These campaigns included the compromise of the ComfyUI_LLMVISION extension on GitHub and the distribution of malicious code through BeamNG mods on Hugging Face and Reddit, such as the maliciously crafted tools ‘SillyTavern Character Generator’ and ‘Image Description with Claude Models and GPT-4 Vision.’
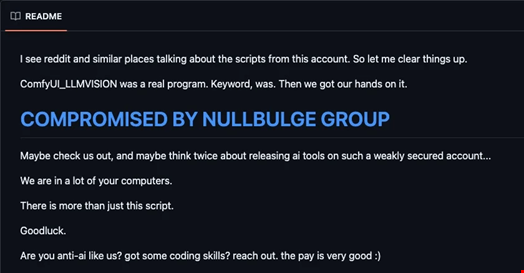
The GitHub and Hugging Face-centric campaigns are characterized by Python-based payloads exfiltrating data via Discord webhook.
The threat actor modified the included ‘requirements.txt’ file to include custom Python wheels to integrate precompiled malicious versions of libraries from Anthropic and OpenAI.
These trojanized libraries contain Python code (e.g., Fadmino.py), which harvests and logs Chrome and Firefox browser data via Network Security Services (NSS). Additional scripts interpret and transmit the data via a Discord webhook URL.
Cybersecurity experts have discussed similarities between NullBulge and AppleBotzz, another persona that conducted malicious activities on AI and software development platforms like Hugging Face, GitHub, ModHub, and ModLand.
NullBulge has denied being linked to AppleBotzz and claimed it took over all accounts previously controlled by AppleBotzz on AI and software development platforms.
According to SentinelLabs, a more probable scenario is that NullBulge controls the AppleBotzz identity, which is central to its malware staging and delivery process.
“However, there’s insufficient evidence to confirm this hypothesis at this time,” the SentinelLabs researchers added.
Low-Skilled Group Using Commodity Malware
One service the group offers on its DLS is described as “payback through honeypots and malicious mods.”
“The group is delivering on this claim by targeting extensions and modifications of commonly used AI-art-adjacent applications and games. This has been their main area of focus recently, delivering a small variety of malware payloads,” the SentinelLabs report reads.
For these campaigns, the group uses tools like Async RAT and Xworm before delivering LockBit payloads built using the leaked Lockbit Black builder.
However, Secureworks assessed that NullBulge operators are not working for LockBit or another group as ransomware-as-a-service (RaaS) affiliates tend not to create their own blogs and social media posts.
According to SentinelLabs, this use of commodity malware and ransomware shows that NullBulge is a low-skilled group.
