More than half (52%) of critical open source projects contain code written in a memory-unsafe language, according to a new analysis by the Cybersecurity and Infrastructure Security Agency (CISA) in collaboration with government agency partners from Australia and Canada.
The Exploring Memory Safety in Critical Open Source Projects joint report investigated the scale of memory safety risk in open source software.
It analyzed a list of 172 projects derived from the Open Source Security Foundation (OpenSSF) Securing Critical Projects Working Group’s List of Critical Projects.
The report concluded that most critical open source projects potentially contain memory safety vulnerabilities. This is a result of direct use of memory unsafe languages or external dependency on projects that use memory-unsafe languages.
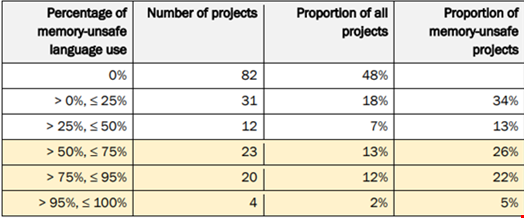
The agencies observed that 55% of the total lines of code (LoC) for all projects were written in a memory-unsafe language.
These projects include operating system kernels and drivers, cryptography and networking.
Each of the 10 largest projects by total LoC had a proportion of memory-unsafe LoC above 26%.
Four of the 10 largest project exceeded 94% memory-unsafe LoC.
Security Risks from Memory Unsafe Languages
The new analysis follows a White House report published in February 2024, which called on the tech industry to adopt memory safe programming languages.
The Office of the National Cyber Director (ONCD) report cited research showing that up to 70% of Common Vulnerabilities and Exposures (CVE) relate to memory safety issues, such as buffer overflows, which could be eliminated by adopting memory safe programming languages, such as Rust.
Currently, the majority of code is written in memory unsafe languages, like C and C++. This means such code is generating substantial patching and incident response costs for software manufacturers and consumers.
Speaking to Infosecurity, Jack Cable, Senior Technical Advisor at CISA, said that memory safety issues are the most dangerous class of vulnerabilities in software today.
“We continue seeing many of the most dangerous exploits leveraging memory safety vulnerabilities,” he commented.
The type of code used in open-source software, which is prevalent across all sectors, is challenging to enforce as it is created by an ecosystem of individuals.
Governments in the US, UK and EU are currently engaging with the open source community to develop workable security regulations for this ecosystem.
Transitioning to Memory Safe Languages
The new report highlighted the challenges of shifting away from memory unsafe languages in open source projects.
“Where performance and resource constraints are critical factors, we have seen, and expect the continued use of, memory-unsafe languages,” the report stated.
However, it was noted that recent advancements in memory-safe languages such as Rust can parallel the performance of memory-unsafe languages.
Cable acknowledged there are challenges to moving away from the current dependency on C and C++ languages, but urged manufacturers to develop memory safety road maps to plan for this journey.
“They need to think in a prioritized manner about how they're going to reduce this class of vulnerability across their product, whether it's rewriting existing critical code that is on a network edge, or committing to write new code, new products in memory safe languages,” he said.
