More than 100 Ukrainian government computers have been compromised following a mass phishing campaign, the Computer Emergency Response Team of Ukraine (CERT-UA) has warned.
The attackers impersonated the Security Service of Ukraine in the emails to lure targets into clicking on a malicious link that leads to ANONVNC malware being downloaded onto the device.
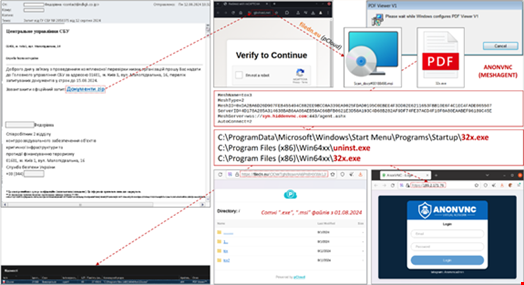
The link purportedly enables the user to download a file named "Документи.zip", translated as “Documents.zip.”
Instead, clicking the link will enable an MSI file to be downloaded to the computer, opening the file will launch ANONVNC.
CERT-UA said ANONVNC is based on an open-source configuration tool MESHAGENT, the source code of which is available on GitHub. This malware creates “technical opportunities” for attackers to gain hidden unauthorized access to the infected computer, the agency added.
The activity is being tracked the identifier UAC-0198.
CERT-UA said it has taken urgent measures to prevent cyber incidents arising from this campaign.
Ukrainian Organizations Targeted by Sophisticated Attacks
CERT-UA warned that cyber-attacks related to this campaign have been carried out since at least July 2024 and may have a “wider geography.” Since August 1, over 1000 EXE and MSI files have been placed in the directories of Ukraine’s pCloud encrypted file storage service alone.
On July 24, the agency revealed a group tracked as UAC-0102 was targeting employees of government agencies, military personnel and other Ukrainian organizations through phishing attacks propagating HTML attachments that mimic the login page of email service domain UKR.NET to steal users' credentials.
In June 2024, FortiGuard Labs highlighted an advanced multi-stage campaign delivering the Cobalt Strike payload to Microsoft Windows systems in Ukraine.
Read now: Russia Shifts Cyber Focus to Battlefield Intelligence in Ukraine
