Published vulnerabilities rose by 43% in H1 2024 compared to H1 2023, with attackers heavily targeting flaws in virtual private networks (VPNs) and other perimeter devices for initial access, a new report from Forescout has found.
A total of 23,668 vulnerabilities were reported in the first six months of 2024, with an average of 111 new CVEs per day.
The majority of published vulnerabilities in H1 2024 had either a medium (39%) or low (25%) severity score (CVSS), while just 9% had a critical score.
This is in contrast to the same period last year, where around two-thirds of vulnerabilities were either medium (39%) or high (27%).
The report also highlighted that 87 CVEs were added to the US Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) catalog in H1 2024, bringing the total to 1140 vulnerabilities. This represents a decrease of 23% compared to the same period in 2023.
The new vulnerabilities published in the catalog in H1 2024 affected 39 different vendors, a 17% decrease from 47 in H1 2023. The most commonly impacted company was Microsoft (17%), followed by Google (8%), Apple (6%), D-Link (6%), Ivanti (6%), Android (5%) and Cisco (5%).
Nearly half (46%) of the vulnerabilities added this year were published before 2024. Five of these flaws were in end-of-life products affecting Internet Explorer, D-Link routers and network attached storage products, meaning no patches are available for this equipment.
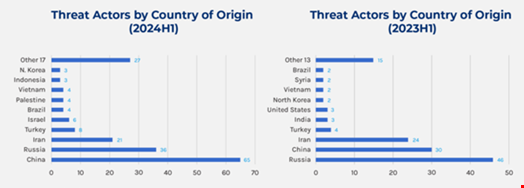
Most Threat Actors Originate from China, Russia and Iran
Forescout found that most threat actors active in H1 2024 originated from China (65), Russia 36%) and Iran (21), with China overtaking Russia from H1 2023.
Half (50%) of these actors are designated as cybercriminals, followed by state-sponsored actors (40%) and hacktivists (10%).
The researchers noted that there are increasingly blurred lines between hacktivists and state-sponsored actors targeting critical infrastructure, with state-sponsored actors using hacktivist personae to conduct some of their attacks.
This shift may be driven by several factors, such as increased visibility of campaigns and plausible deniability for the actors.
An example of this type of threat actor is the Cyber Army of Russia, believed to be linked to Sandworm, which launched an attack against a wastewater treatment plant in the US in April 2024.
Another is Predatory Sparrow, which poses as a hacktivist group rebelling against the Iranian state, but is believed to be affiliated with Israel.
Read now: From Protests to Profit: Why Hacktivists Are Joining the Ransomware Ranks
Ransomware Attacks Continue to Rise
The report showed a 6% rise in ransomware attacks in H1 2024 compared to H1 2023, reaching 3085 attacks.
The ransomware landscape has significantly fragmented over this period – in H1 2023, the top 10 groups accounted for three quarters of attacks, but in H1 2024 they represented 59%.
LockBit was the most active group in this period, responsible for 15% of attacks. This is despite the significant law enforcement operation targeting the group’s infrastructure in February 2024.
LockBit was followed by Play (6%), RansomHub (6%), Cactus (5%), Akira (5%), Hunters (5%) and BlackBasta (5%).
