The average extortion demand per ransomware attack was over $5.2m (£4.1m) in the first half of 2024, according to a new analysis by Comparitech.
This figure was calculated from 56 known ransom demands issued by threat actors from January-June 2024. The biggest of these was a $100m (£78.9m) ransom following an attack on India’s Regional Cancer Center (RCC) in April 2024.
The second highest confirmed ransom demand was issued to UK pathology provider Synnovis, with attackers demanding $50m (£39.4m) from the company. This incident led to thousands of operations and appointments being cancelled at hospitals in South East England. The Qilin group has claimed to have stolen 400GB of data in the attack, including sensitive NHS patient medical records.
The third highest ransom demand in H1 2024 was sent to Canadian retailer London Drugs following an attack in May 2024, with the LockBit group demanding $25m (£19.7m) in payment.
Over 35 Million Records Stolen in Ransomware Attacks
The researchers logged 421 confirmed ransomware attacks in H1 2024, impacting around 35.3 million records. These figures represent a reduction compared to the same period in 2023, in which 704 attacks affecting 155.7 million records were recorded.
However, breach disclosures for H1 2024 will continue, so these figures are likely to increase.
Comparitech also said it has logged a further 1920 attacks that have been claimed by ransomware gangs but not acknowledged by the alleged victims.
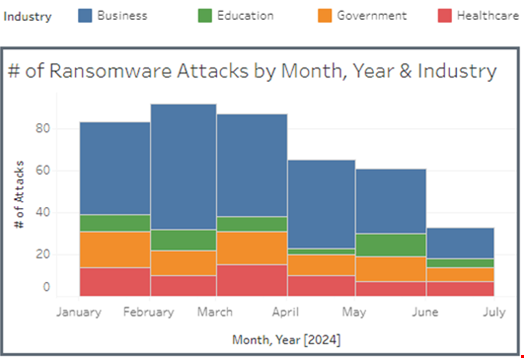
Private businesses experienced 240 incidents impacting 29.7 million records, according to the analysis of confirmed attacks in the six months since January 2024.
This is followed by government, with 74 attacks impacting 52,390 records, and healthcare, with 63 attacks affecting 5.4 million records.
Read here: How to Respond Effectively During a Ransomware Attack
The top five ransomware incidents in H1 2024 by number of individual records affected were:
- LoanDepot– 16.9 million records
- Izumi Co – 7.7 million records
- Prudential Insurance – 2.5 million records
- India’s Regional Cancer Center (RCC) – 2 million records
- Ann & Robert H. Lurie Children’s Hospital of Chicago – 791,784 records
LockBit Remains Most Prolific Ransomware Group
Notorious ransomware-as-a-service (RaaS) operator LockBit was responsible for the highest number of confirmed attacks in H1 2024, at 48.
This is despite a significant law enforcement operation that took down the group’s infrastructure in February.
Following a period of apparent dormancy, LockBit operators appear to have resurfaced, with an analysis by NCC Group finding it was by far the most prominent ransomware group in May 2024.
The next most prominent group in the first half of 2024 according to Comparitech was Medusa (31 attacks), followed by BlackBasta (27), Akira (20), 8Base (17) and INC Ransom (16).
The researchers also observed an increase in groups who no longer encrypt files as part of their attack and instead rely solely on data theft for extortion.
Read here: Ransomware Ecosystem Transformed, New Groups “Changing the Rules”
