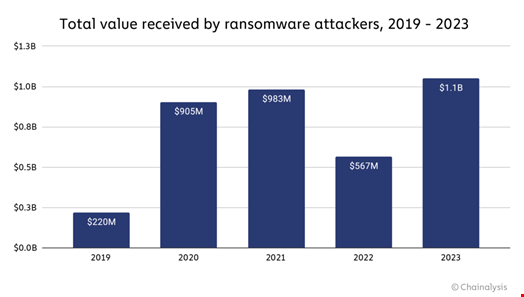
Ransomware actors collected over $1bn in extortion money from their victims in 2023 – a record high – according to Chainalysis.
The blockchain analysis company warned that even this is likely to be a conservative estimate of the financial impact of ransomware last year, as new cryptocurrency addresses are likely to be discovered over time. It said the figure for 2022 has already been revised up 24% to $567m, for example.
The figure also does not capture other costs associated with ransomware breaches, such as operational disruption, lost custom and expenses related to third-party incident response and forensics.
Two new regulatory filings from victims Clorox and Johnson Controls late last week revealed an initial combined cost of $76m related to two serious breaches at the companies last year.
Ransomware payments have been on the rise since 2019 when Chainalysis began recording the market, aside from a dip in 2022.
However, 2023 saw a “major escalation in the frequency, scope and volume of attacks,” driven by a surge in the number of groups carrying out attacks. These groups were “attracted by the potential for high profits and lower barriers to entry,” the report revealed.
It claimed big-game hunting from groups like Clop has become the “dominant strategy” over recent years, with more and more payments of $1m or more showing up. Ransomware-as-a-service (RaaS) also continues to have an outsized impact in drawing in more affiliates – many of which target smaller victims with lower ransoms.
As has been the case for several years, the ready availability of hacking tools and initial access broker (IAB) services made their job even easier last year. In the case of big-game hunters, exploitation of zero-day vulnerabilities became more popular, such as in the infamous MOVEit campaign, the report continued.
The past year saw an increase in the use of bridges, instant exchangers and gambling services – alongside centralized exchanges and mixers – as a preferred method of laundering funds.
“We assess that this is a result of takedowns disrupting preferred laundering methods for ransomware, some services’ implementation of more robust AML/KYC policies, and also as an indication of new ransomware actors’ unique laundering preferences,” the report noted.
Takedowns Do Work
However, the lessons of 2022 may hold out some hope for those looking to disrupt this burgeoning cybercrime industry.
Although the Russia-Ukraine conflict had an impact on ransomware activity that year, so did successful infiltration of the Hive ransomware group.
“The FBI’s $130m reduced payment estimate may not tell the whole story of just how successful the Hive infiltration was. That figure only looks directly at ransoms averted through the provision of decryptor keys, but does not account for knock-on effects,” Chainalysis argued.
“The Hive infiltration also most likely affected the broader activities of Hive affiliates, potentially lessening the number of additional attacks they could carry out.”
