Hackers are deep in the spirit of exploiting the holidays for financial gain, which is why it’s unsurprising that yet another new type of spear phishing attack has emerged, in which attackers are posing as CEOs to trick office managers, executive assistants and receptionists into sending them gift cards, according to email security researchers at Barracuda Networks.
Since early October, the researchers have reportedly seen an uptick in these types of attacks. Unlike other phishing campaigns that include attachments, these emails do not have malicious links or files included. What also seems to be working effectively is that they are often sent from trusted email domains.
As a result, traditional email filters often do not recognize them as threats. Additionally, the attackers capitalize on the urgency of the holidays and poses the request as a company surprise to discourage the victim from confirming the legitimacy of the request.
Using the social engineering tactics of CEO impersonation, requests for secrecy, researching relevant details and implied urgency, the attackers are specifically and intentionally exploiting people’s good cheer during the holidays.
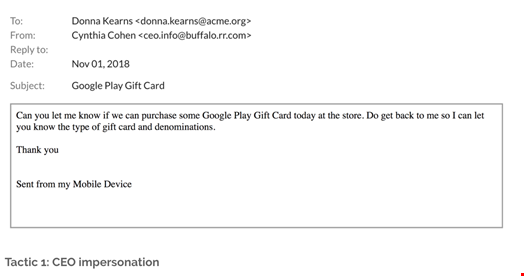
In another example, an email message sent “from my Sprint Wireless 4G LTE Smartphone” asks the recipient to pick up gift cards to be distributed to staff but requests that she keep the transaction confidential.
“In all of these attacks, the emails were sent from free personal email services with a relatively high reputation. In addition, they do not contain any type of malicious payload, such as links or attachments,” wrote Barracuda’s Asaf Cidon, VP of content security services.
“Instead the emails rely solely on social engineering and impersonation to trick their targets. These types of attacks are very hard for traditional email filters to pick up because they are targeted, have a high reputation, and do not contain any obvious malicious signals.”
