Russian cyber espionage group Secret Blizzard has used the tools and infrastructure of at least six other threat actors during the past seven years, according to Microsoft.
In a December 4 report, Microsoft Threat Intelligence shared new findings about Secret Blizzard, an advanced persistent threat (APT) group that has been attributed by the US Cybersecurity and Infrastructure Security Agency (CISA) to Center 16 of Russia’s Federal Security Service (FSB).
The group, also known by other names, such as Turla, Iron Hunter, Venomous Bear, WhiteBear Waterbug or Snake, has been active since at least 2004.
It has targeted a wide range of verticals, but most prominently ministries of foreign affairs, embassies, government offices, defense departments and defense-related companies worldwide.
Its typical tactics include the use of watering holes, adversary-in-the-middle (AiTM) attacks and spear-phishing campaigns, leveraging in-house tools and malware like Uroburos.
However, Microsoft has now revealed that the group has also been extensively piggybacking on other threat actor’s infrastructure and using other groups’ tools to conduct its operations.
The Microsoft researchers observed that Secret Blizzard had used at least six other groups’ infrastructure and tools over the past seven years, including cybercriminals and other cyber espionage groups.
Additionally, Secret Blizzard has actively targeted infrastructure where other threat actors have staged exfiltrated data from victims to collect this data for their own espionage program.
Previous Evidence of Secret Blizzard “Borrowing” Tools
While not unique, this behavior is “a somewhat unusual attack vector for threat actors in general,” Microsoft noted.
Several vendors had observed standalone events where Secret Blizzard had previously exploited other threat actors’ tools. These included:
- Accessing tools and infrastructure of Iranian state-sponsored threat actor Hazel Sandstorm (aka OilRig, APT34, Crambus) in 2017 (Symantec, US and UK intelligence services)
- Reusing Andromeda malware to deploy the KopiLuwak and QuietCanary backdoors in 2022 (Google Cloud’s Mandiant)
- Using the backdoor of the Kazakhstan-based threat actor tracked by Microsoft Threat Intelligence as Storm-0473, also called Tomiris, in an attempt to deploy QuietCanary in 2022 (Kaspersky)
However, Microsoft’s latest report showed the extent to which Secret Blizzard had been leveraging other groups’ infrastructure was significantly greater than previously imagined.
Piggybacking on Pakistani APT Storm-0156
Microsoft analyzed how Secret Blizzard has been compromising the command-and-control (C2) infrastructure of a Pakistan-based espionage cluster tracked as Storm-0156 since November 2022.
“Secret Blizzard has used Storm-0156’s backdoors to deploy [its] own backdoors to compromised devices. In addition, Secret Blizzard tools have been deployed to virtual private servers (VPS) staging Storm-0156’s exfiltrated data.”
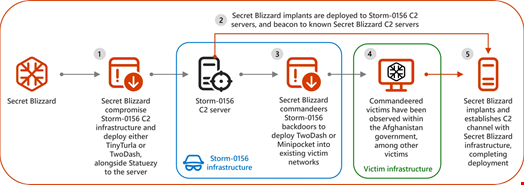
Secret Blizzard's tactics include deploying its own backdoors, such as TinyTurla, TwoDash, Statuezy and MiniPocket onto Storm-0156's C2 servers.
The group has also confiscated Storm-0156's backdoors, like CrimsonRAT and Wainscot, to further their own objectives.
Additionally, Secret Blizzard has employed various techniques, such as DLL side-loading and search order hijacking, to execute malicious payloads on compromised devices.
This sophisticated cyber espionage campaign highlights the increasing complexity of threat actor tactics, according to Microsoft. By piggybacking on other groups' infrastructure, Secret Blizzard can operate more stealthily and efficiently, making detecting and disrupting their activities challenging.
