In a world-first, a Russian state-sponsored hacking group has used software vulnerability exploits “identical or strikingly similar” to ones previously used by NSO Group and Intellexa, two infamous commercial spyware vendors.
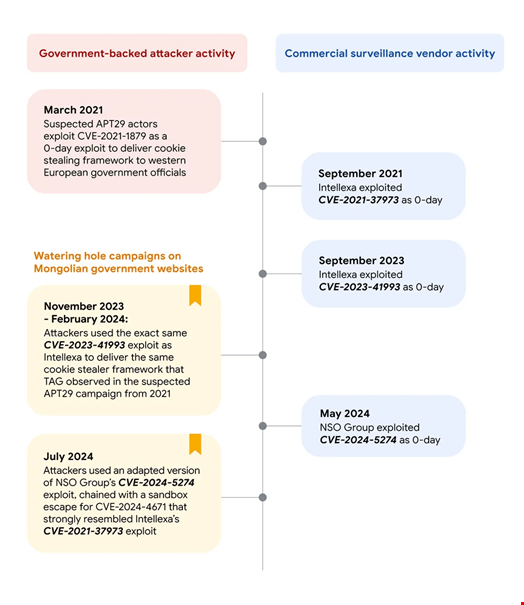
In a new report, Google Threat Analysis Group (TAG) shared insights on two watering hole attacks targeting Mongolian government websites between November 2023 and July 2024.
A watering hole is a website or platform frequented by a specific target group that hackers use to distribute malware or exploit vulnerabilities.
Google assessed “with moderate confidence” that the campaigns were conducted by the Russian-sponsored group APT29.
Watering Hole Attacks Targeting Safari and Google Chrome
The hacker compromised the cabinet.gov[.]mn website from November 2023 and the mfa.gov[.]mn website first in February 2024 and then in July 2024.
The campaigns took advantage of vulnerabilities in Apple’s Safari browser and Google Chrome on Android.
The first delivered an iOS WebKit exploit (via CVE-2023-41993) in order to steal user account cookies stored in Safari. This campaign affected iOS versions older than 16.6.1.
The second delivered a Chrome exploit chain (via CVE-2024-5274 and CVE-2024-4671) against Android users running versions from m121 to m123.
Although these vulnerabilities had already been fixed at the time the campaigns occurred, Google noted that they would still be effective against unpatched devices.
Exploits Previously Used by Spyware Vendors
Each of the three vulnerabilities had been exploited before by either NSO Group, an Israeli company developing Pegasus spyware, or Intellexa, a Greece-based firm that is part of a private consortium of surveillance solutions vendors and the maker of Predator spyware.
This is one of the first occurrences of a state-sponsored hacking group reusing commercial spyware vendors’ intrusion techniques.
“While we are uncertain how suspected APT29 actors acquired these exploits, our research underscores the extent to which exploits first developed by the commercial surveillance industry are proliferated to dangerous threat actors,” the report states.
The Google TAG team notified Apple, Alphabet’s Android and Google Chrome units and the the Mongolian computer emergency response team (CERT) about the campaigns at the time of discovery.
Read more: How to Mitigate Spyware Risks and Secure Your Business Secrets
