A pro-Russian hacktivist group has launched its own ransomware-as-a-service (RaaS) operations to advance its causes.
Researchers from SentinelLabs has observed the CyberVolk hacktivist collective advertise its branded ransomware since June, 2024, and has claimed responsibility for multiple ransomware attacks between June and October.
The hacktivist group, which originated in India, has also promoted and shared tools with other ransomware families.
The analysis highlights the growing blurring of the lines between hacktivism, cybercrime and nation-state activity.
The researchers noted that the group’s activities also demonstrate how readily threat actors can access and deploy dangerous ransomware builders, making such groups increasingly challenging to track.
Read now: Threat Actors Weaponize Hacktivism for Financial Gain
Exploiting Geopolitical Issues to Target Governments
SentinelLabs said that CyberVolk emerged in its current form in May 2024, prior to which it was known by various names including Gloriamist, Gloriamist India and Solntsevskaya Bratva.
The collective has pro-Russia leanings and leverages geopolitical issues to launch and justify attacks on public and government entities opposed to Kremlin interests.
It has become a prominent player in the cybercrime ecosystem, utilizing DDoS attacks as well as adopting and repurposing existing commodity malware to advance its operations. These include infostealer malware and webshells.
CyberVolk claims alliances with a range of hacktivist and cybercrime groups, including Lapsus$, and the Moroccan Dragons.
CyberVolk Launches Branded Ransomware
In June, CyberVolk announced its branded RaaS capabilities. The researchers said this ransomware is derived from AzzaSec ransomware code. AzzaSec is a pro-Russia, anti-Israel, and anti-Ukraine hacktivist group that emerged in February 2024.
The source-code for AzzaSec Ransom was leaked and subsequently adopted and adapted by multiple groups aligned with AzzaSec’s mission in June 2024.
The CyberVolk-modified version of the ransomware uses Windows-specific payloads that are written in C++. It is designed to terminate any running processes belonging to either Microsoft Management Console (MMC) or Task Manager.
Upon execution, the payloads drop bitmap images (files with extension .bmp) into %temp% folder, and display them, prior to any encryption occurring.
According to posts on CyberVolk’s Telegram account, the algorithms used for encryption and key generation was updated from AES and SHA512, respectively, to “ChaCha20-Poly1305 + AES + RSA + Quantum resistant algorithms.”
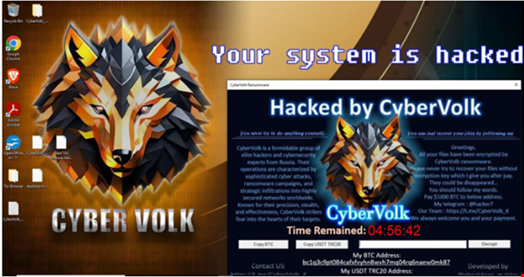
When a victim’s files have been encrypted, a payment screen is displayed showing the decryption timer along with payment details, with payment accepted in cryptocurrencies.
The timeout is set to five hours in CyberVolk samples analyzed by SentinelOne.
Telegram contact details are also provided in the payment screen.
The researchers said that CyberVolk has recently utilized its branded ransomware payloads in attacks against entities in Japan, including the Japan Meteorological Agency (JMA) and the Tokyo Global Information System Centre.
These attacks have been “hyped up” across various channels used by the group, such as Telegram and Discord.
Affiliations with Other Ransomware Families
The researchers have also observed CyberVolk associations with other ransomware families. This includes promoting “Doubleface,” which emerged in August-September 2024.
Doubleface ransomware is derived from the same AzzaSec Ransomware code base used by CyberVolk, and the payloads function in an identical manner to CyberVolk-branded ransomware samples.
Additionally, CyberVolk has promoted HexaLocker and Parano ransomware families.
In early November, CyberVolk and numerous affiliated groups, including Doubleface, vanished from Telegram as a result of a mass ban of hacktivist groups, following a commitment from founder and CEO of the platform Pavel Durov.
The case of CyberVolk demonstrates the dynamic nature of affiliations and alliances between hacktivist groups. The researchers noted that regular infighting and tensions among them also fuel for the rates of growth and change, making it more challenging for cyber defenders to track their activities consistently.
