A spear-phishing email campaign targeting government entities in Ukraine could have been active as early as 2014, according to FireEye.
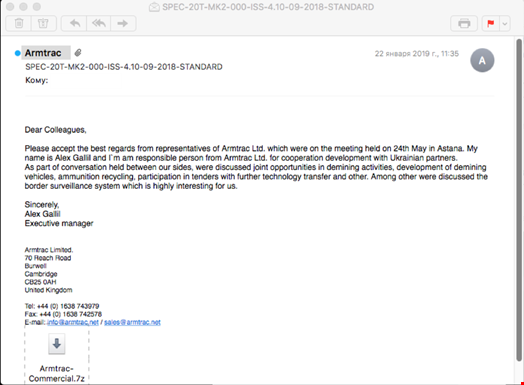
In a blog post published on April 16, 2019, FireEye Threat Intelligence found the latest spear-phishing email in early 2019, which included a "malicious LNK file" with PowerShell script to download the second-stage payload from the command-and-control (C&C) server. The email was received by military departments in Ukraine and included lure content related to the sale of demining machines.
According to FireEye, "This latest activity is a continuation of spear phishing that targeted the Ukrainian Government as early as 2014." The company also wrote that the infrastructure analysis indicated the actors behind the intrusion activity may be associated with the so-called Luhansk People's Republic (LPR).
The email, sent on January 22, 2019, used the subject "SPEC-20T-MK2-000-ISS-4.10-09-2018-STANDARD," and the sender was forged as Armtrac, a defense manufacturer in the United Kingdom. An attachment included a 7z package with two benign documents and a one malicious LNK file.
"Compilation times indicate that this actor, who focused primarily on Ukraine, may have been active since at least 2014," the blog post says. "Their activity was first reported by FireEye Threat Intelligence in early 2018. They gradually increased in sophistication and leveraged both custom and open-source malware."
Ukraine legislation describes so-called LPR as "temporarily occupied territory" and its government as an "occupying administration of the Russian Federation," according to FireEye.
"While cyber-espionage is regularly leveraged as a tool of state power, this capability is not limited to states," said John Hultquist, director of analysis, FireEye. "Just as new state actors are consistently drawn to this practice, many sub-state actors will inevitably develop capabilities as well, especially those with the resources of a state sponsor or nominal control of territory.
"It is not uncommon for nascent, geographically limited operations to mature over time and step outside of their region. This has been the case with several actors we regularly track in the Ukraine, where threats to elections and industry developed into the operations we saw during the 2016 elections and the NotPetya event."