Cryptocurrency mining has become a fairly easy way to manufacture currency, and according to Trend Micro, a new cryptocurrency-mining malware uses evasion techniques, including Windows Installer, as part of its routine.
In the cryptocurrency miner identified as Coinminer.Win32.MALXMR.TIAOODAM, researchers noted the use of multiple obfuscation and packing routines. The malware leverages the Windows platform, and though it has an overall low risk rating, the damage potential scored in the medium range.
While the results might be lucrative, the process is actually quite resource-intensive, which is one reason malicious actors continue to find ways to exploit other machines using mining malware. These malware have been largely successful in avoiding detection, particularly when combined with obfuscation routines, according to Trend Micro.
If you found this article insightful, why not watch our #InfosecWebinar on Malware in IoT, Crypto-coins & Smart Devices
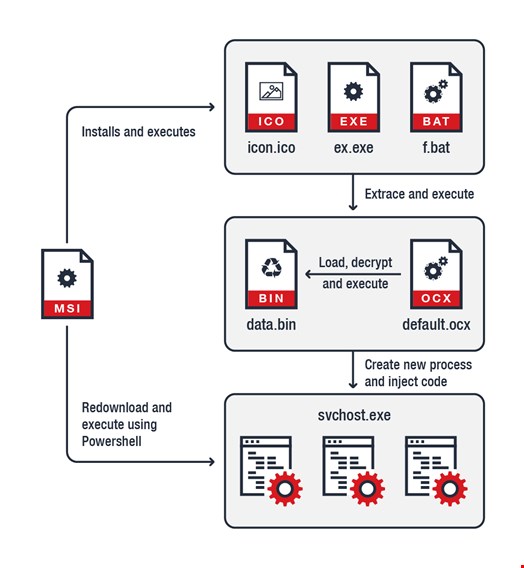
Dropped by other malware or downloaded from the internet, the coinminer infects the user system after arriving as a Windows Installer MSI file. It then drops multiple files in the directory as part of its process and uses the CryptoNight algorithm for its coin-mining routing. Included in the files are a .bat file that shuts down any anti-malware program running on the machine, an .exe unzipping tool and a password-protected zip file that appears to be an icon (.ico) file.
Two additional files were revealed after the icon.ico was unpacked before the next part of the installation process began creating copies of the kernel file and a Windows USER component. Researchers noted that the installation uses Cyrillic rather than English text, though there is no concrete evidence indicating the region of origin.
“To make detection and analysis even more difficult, the malware also comes with a self-destruct mechanism,” the authors wrote. “It deletes every file under its installation directory and removes any trace of installation in the system. One notable aspect of the malware is that it uses the popular custom Windows Installer builder WiX as a packer, most likely as an additional anti-detection layer. This indicates that the threat actors behind it are exerting extra effort to ensure that their creation remains as stealthy as possible.”
