Using consumer data stolen in data breaches and made available on the dark web, cyber-criminals have launched a sextortion phishing campaign, according to research from Barracuda Networks.
In this month's Threat Spotlight, researchers detail the sextortion scam in which attackers prey on victims by using stolen passwords, threatening that they have a compromising video that will be shared with the victim’s contacts unless the user pays in Bitcoin.
The campaign started in July, and Barracuda Labs said it remains ongoing. Researchers found roughly 24,000 emails reported by customers around the globe since September. The emails reportedly use the stolen password as the subject line, though some might precede it with “your password is.”
Preying on human fear, the attackers know the impact that such a subject will have at the mere suggestion that their account has been hacked. According to the research findings, the email goes on to claim that the user's computer was infected with a remote access Trojan (RAT) from a pornography website. The claim is that all of the explicit videos the user has been watching have been recorded.
“The email also claims that the user’s contacts from email and social networking have been gathered and that unless a sum of money is paid (in Bitcoin, of course), the video of the user watching porn will be sent to those contacts. We also saw examples of the attackers emailing the same address multiple times to up the scare tactics, an approach they are likely taking with most if not all of their intended victims,” wrote Jonathan Tanner in the Threat Spotlight.
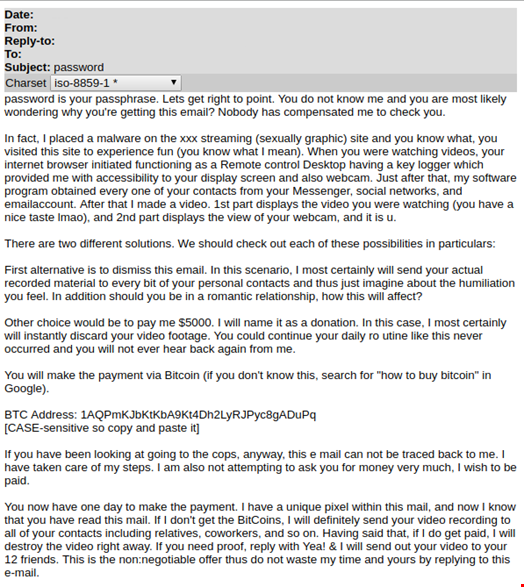
While the attacker does have a legitimate password, which researchers said was likely from a list made public in 2016 of more than 500 million leaked passwords, there is no video, nor has any infection been found on victim computers.
“Whether or not the user has visited any pornographic websites is something only they know, but given that these emails are largely targeting business emails it's unlikely they're doing so on their work computer. For obvious reasons, we didn't send out a survey asking as much, but it seems safe to assume, and thus the other claims in the email must also be false,” Tanner wrote.
