A recent analysis has shed light on the extent of phishing and smishing attacks targeting the United States Postal Service (USPS), particularly during the holiday season.
The study, conducted by Akamai Security researchers using anonymized global DNS query logs, revealed a startling trend. Illegitimate domains mimicking USPS websites attracted nearly equal, and sometimes higher, traffic compared to legitimate domains, especially during peak shopping periods like Thanksgiving and Christmas.
The research efforts, published in an advisory last Thursday and undertaken by a team examining DNS-level activity related to the USPS website, began by identifying malicious domains associated with confirmed fraudulent JavaScript files and HTML patterns resembling scam messages.
Through filtering criteria, domains containing the string “USPS” were isolated, resulting in a dataset reflecting malicious intent. Notably, the study took great care to avoid false positives, ensuring accuracy in the analysis.
The findings unveiled a plethora of deceptive domains, employing techniques such as combo squatting, wherein familiar brand names like USPS are exploited to evoke trust in victims. Among the top malicious domains were “usps-post[.]world” and “uspspost[.]me,” each attracting over 100,000 hits, highlighting the efficacy of these campaigns.
Read more on similar attacks: New Typosquatting and Repojacking Tactics Uncovered on PyPI
Furthermore, analysis of top-level domains (TLDs) revealed common choices among threat actors, with “.com” and “.top” domains dominating the landscape. Interestingly, while the “.com” TLD provided global legitimacy, “.top” emerged as a popular alternative known for its association with malicious activities among security researchers.
In terms of IP addresses, distinct patterns emerged. Some IPs hosted few domains but received significant traffic, while others hosted numerous domains with lower individual traffic. This diversity suggests varying strategies employed by cybercriminals to evade detection.
Comparisons between legitimate USPS traffic and malicious domains highlighted alarming similarities in query counts, especially during holidays, indicating a significant threat to consumers.
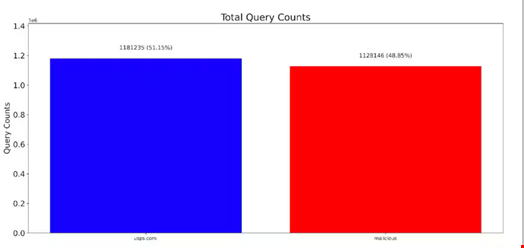
The technical write-up concludes by urging continued monitoring and reporting of such threats, both to safeguard consumers and inform broader cybersecurity efforts.
