Cybercriminals are using a wider-than-ever range of malicious documents to spread malware and gain initial access to target systems, according to HP Wolf Security.
Alex Holland, principal threat researcher in the HP Security Lab, told Infosecurity that threat actors have recently shifted their focus.
They are now prioritizing script-based phishing techniques over approaches based on traditional malicious documents, he said ahead of the launch of HP Wolf Security’s Threat Insights Report Q2 2024.
Leveraging Archive Files in Phishing Campaigns
“For the past two years, we have seen a movement away from using maldocs, Microsoft Office documents containing malicious macros, towards leveraging interpreted script languages, such as VBScript and JavaScript,” Holland explained.
Typically, threat actors would combine this living-off-the-land phishing technique with delivering encrypted archive files.
“With this approach, instead of sending an attached document that includes a malicious macro infecting the target system, threat actors would send an archive file that includes hidden malicious VBScript or JavaScript code alongside the file that the victim wants to download.”
HP Wolf Security’s quarterly report shows that 39.23% of malware deliveries came from an archive file in the second quarter of 2024, compared to 27.89% in the previous reported period.
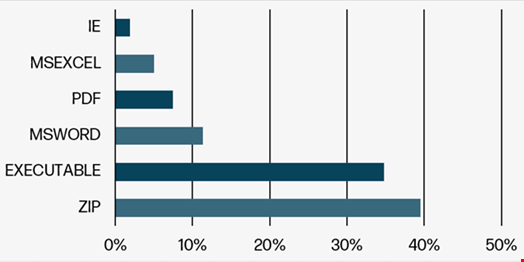
This approach, which Holland considers of a higher sophistication level than traditional phishing techniques, is made possible by the high number of archive file formats that can be used.
“Although most people would only know the main formats, such as WinZip, 7-zip or WinRar, we have found in our latest report that threat actors have used 50 different archive file formats to deploy phishing campaigns,” Holland noted.
He added that this is partly because Windows 11 supports more archive file formats than its predecessors.
“We recommend that organizations lock down archive file formats they’re not using to reduce the attack surface,” he said.
Evidence of AI-Generated Malicious Code
Other findings from the report include:
- Phishing campaigns using an extensive range of vectors to infect victims, including malicious PDF documents and SVG images
- One malvertising campaign using ChromeLoader, a malicious browser extension that targets Google Chrome and other Chromium-based browsers to redirect users to unwanted websites, often those promoting advertisements or malicious content
- HP Wolf’s first evidence of generative AI being used in a malicious campaign
This latter finding refers to a campaign targeting French speakers using VBScript and JavaScript that HP Security Lab researchers believe to have been written with the help of GenAI.
Patrick Schläpfer, another principal threat researcher in the HP Security Lab, explained how his team made this assessment: “The structure of the scripts, comments explaining each line of code, and the choice of native language function names and variables are strong indications that the threat actor used GenAI to create the malware.”
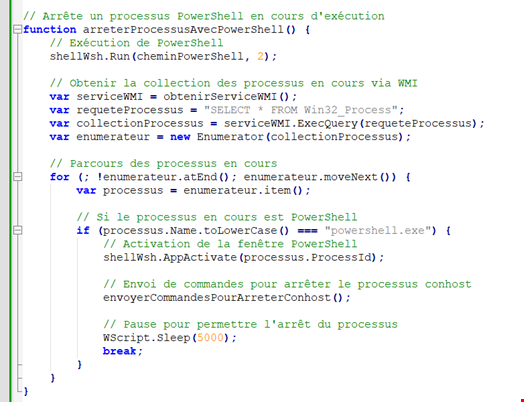
“The attack infects users with the freely available AsyncRAT malware, an easy-to-obtain infostealer that can record victim’s screens and keystrokes. The activity shows how GenAI is lowering the bar for cybercriminals to infect endpoints,” Schläpfer said.
