Cyber-attacks are becoming more frequent and severe, posing a greater risk to British organizations and the public, warned the UK’s National Cyber Security Centre (NCSC) in its latest Annual Review.
The report, published on December 3, shows that the NCSC’s Incident Management (IM) team has intervened 430 times out of the 1957 cyber-incident reports it received over the past year, exceeding the 371 needing the agency’s involvement in 2023.
Of these incidents, 89 were nationally significant, including 12 critical incidents – a threefold increase compared to last year.
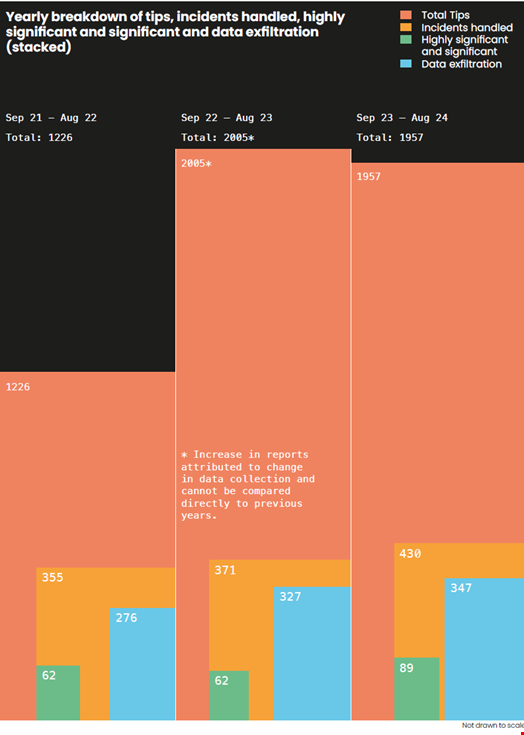
Additionally, the IM team issued 542 bespoke notifications to UK organizations experiencing a cyber incident in 2024, over twice as many as the 258 bespoke notifications issued last year.
New NCSC Chief Urges Stronger Cyber Defenses
Richard Horne, NCSC’s new CEO, is expected to give his first-ever public speech in the role at an Annual Review launch event in London on December 3.
“What has struck me more forcefully than anything else since taking the helm at the NCSC is the clearly widening gap between the exposure and threat we face and the defenses that are in place to protect us,” he said in prepared remarks released ahead of the event, underscoring the urgent need for stronger cyber defenses and increased collaboration to address escalating threats. “And what is equally clear to me is that we all need to increase the pace we are working at to keep ahead of our adversaries.”
Horne believes most UK organizations, public and private, and the general public, are “widely underestimating” the country's cyber threats.
“We need all organizations, public and private, to see cybersecurity as both an essential foundation for their operations and a driver for growth. To view cybersecurity not just as a ‘necessary evil’ or compliance function, but as a business investment, a catalyst for innovation and an integral part of achieving their purpose.”
He is expected to announce that during his time in office, the NCSC will focus on translating previous NCSC guidance and frameworks into practice.
"Defense and resilience of critical infrastructure, supply chains, the public sector and [the UK's] wider economy must improve."
Finally, Horne has told the press that “defense and resilience of critical infrastructure, supply chains, the public sector and [the UK’s] wider economy must improve.”
Pat McFadden MP, Chancellor of the Duchy of Lancaster and Minister for Intergovernmental Relations, said in the report that one way of strengthening the UK’s defenses was by of doing this is by “driving up the adoption of our ‘Cyber Essentials’ scheme. Stats show those businesses who implement Cyber Essentials are 92% less likely to make a claim on their cyber insurance.”
“We are also working closely with businesses and industry through the NCSC and the National Protective Security Authority (NPSA) to offer practical ways that organizations can strengthen their own security and help defend the nation from cyber-attacks,” he added.
Ransomware, the Most Pervasive Threat to the UK
NCSC described ransomware as the most pervasive cyber threat to UK organizations.
Of the 542 bespoke notifications sent in by the IM team 2024, 317 were related to pre-ransomware activity, an increase on 297 in 2023.
These were triaged into 20 NCSC-managed incidents, of which 13 were nationally significant, including cyber-attacks against the British Library and several NHS trusts.
“The ransomware attack on Synnovis, and the impact this had on thousands of procedures and appointments across six NHS trusts, illustrates why – in our increasingly interconnected world – we must remain ahead of the threat,” Anne Keast‑Butler, Director of the UK Government Communications Headquarters (GCHQ), said in the report.
The top targets for ransomware activity in the UK were academia, manufacturing, IT, legal, charities and construction.
Over the last year, the IM team issued approximately 12,000 alerts about vulnerable services through its Early Warning service.
Exploitation of zero-days CVE-2023-20198 (Cisco IOS XE) and CVE-2024-3400 (Palo Alto Networks PAN-OS) also resulted in six nationally significant incidents for the IM team to manage.
Initiatives the NCSC has taken part in to curb the ransomware threat include a joint guidance on ‘ransom discipline’ developed in collaboration with the Information Commissioner’s Office (ICO) and the legal and insurance sectors to reduce the number of ransomware payments being made by victims of cybercrime and the Counter Ransomware Initiative (CRI), an international coalition of 40 members and eight insurance bodies.
Nation-State Campaigns More Frequent and With Greater Impact
Characterizing the 2024 cyber threat landscape as “diffuse and dangerous,” the Annual Review noted a rising frequency of cyber incidents and a growing severity in their impact, especially those coming from nation-state actors.
Over the past 12 months, the NCSC has observed how conflicts are fuelling a volatile threat landscape, including Russia’s deployment of destructive malware against Ukrainian targets and routine attempts to interfere with the systems of NATO countries in support of its war effort.
The Annual Review also noted that Moscow is increasingly inspiring non-state threat actors to carry out cyber-attacks against critical national infrastructure (CNI) in the UK and the Western world.
“These threat actors are not subject to formal or overt state control, which makes their activities less predictable. However, this does not lessen the Russian state’s responsibility for these ideologically driven attacks,” reads the report.
China is described as a highly sophisticated and capable actor targeting various sectors. In February 2024, the NCSC co-signed an advisory on observed compromises of US Critical National Infrastructure (CNI) by Volt Typhoon. In March 2024, the UK government called out China state-affiliated actors for targeting democratic institutions.
Iran-based threat actors remain aggressive in cyberspace, and North Korea continues to prioritize raising revenue to circumvent sanctions and collect intelligence in its cyber activity.
