The US government has sanctioned a Chinese cybersecurity company and one of its employees for their involvement in the large-scale compromise of firewalls in April 2020.
The hacked firewalls were exploited to install malware and deploy ransomware worldwide. Victims included US critical infrastructure firms and could have resulted in serious injury or loss of life.
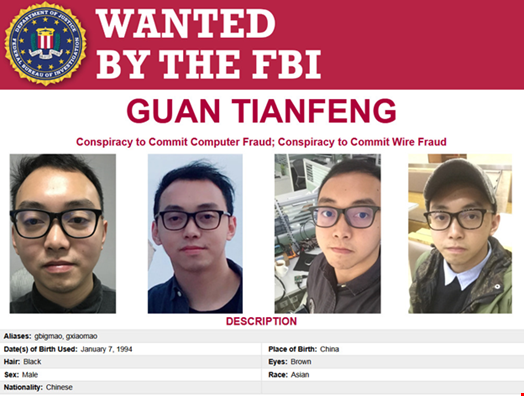
The Department of the Treasury’s Office of Foreign Assets Control (OFAC) indicted Sichuan Silence Information Technology Company, Limited (Sichuan Silence) and its employee Guan Tianfeng (Guan) for discovering and exploiting a zero-day exploit in a firewall to launch the attacks.
Sichuan Silence is a cybersecurity government contractor specializing in offensive techniques, its core clients are People’s Republic of China (PRC) intelligence services.
Guan was a security researcher at the firm at the time of the compromise. He posted recently discovered zero-day exploits on vulnerability and exploit forums under his moniker GbigMao.
The sanctions mean that any money or assets owned by Sichuan Silence or Guan in the US must be blocked and reported to OFAC.
A reward of up to $10m has also been offered by the US Department of State for information about Sichuan Silence or Guan.
Read now: Massive Telecom Hack Exposes US Officials to Chinese Espionage
Firewall Vulnerability Used to Steal Data and Deploy Ransomware
OFAC said that Tianfeng used this zero-day exploit to deploy malware to approximately 81,000 firewalls owned by thousands of businesses worldwide between April 22 and 25, 2020.
More than 23,000 of these firewalls were in the US, with 36 protecting US critical infrastructure companies’ systems.
The SQLi vulnerability, designated as CVE 2020-12271, was used alongside a command injection privilege escalation to gain root access to the device and install the Asnarök Trojan.
The purpose of these attacks was to steal data including usernames and passwords from the compromised firewalls. Additionally, Guan attempted to infect the victims’ systems with the Ragnarok ransomware variant.
The US believes if the victim critical infrastructure victims had failed to mitigate the exploit or remedy the intrusion, the Ragnarok ransomware attack could have resulted in serious injury or the loss of human life.
For example, had a US energy company involved in active drilling operations not thwarted the attack, it could have caused oil rigs to malfunction.
Chinese Groups Persistently Targeting Perimeter Devices
There is a wider trend of Chinese threat actors targeting perimeter devices to compromise multiple organizations, including US government agencies and critical infrastructure firms.
In October 2024, cybersecurity company Sophos set out a five-year investigation tracking interlocking campaigns by China-based groups targeting perimeter devices from 2018-2023, dubbed ‘Pacific Rim.’
This identified notable attacks during this period, which involved attackers discovering and exploiting zero-day vulnerabilities across widely used perimeter devices. These attacks led to the deployment of different malware and sophisticated tools designed to bypass security controls.
Ross McKerchar, CISO at Sophos, welcomed OFAC’s sanctions, emphasizing the need for innovation and collaboration to tackle the threat posed by PRC groups.
"The scale and persistence of Chinese nation-state adversaries poses a significant threat to critical infrastructure, as well as unsuspecting, everyday businesses as noted in Sophos’ Pacific Rim investigation report. Their relentless determination redefines what it means to be an Advanced Persistent Threat; disrupting this shift demands individual and collective action across the industry, including with law enforcement,” he noted.
“We can’t expect these groups to slow down, if we don’t put the time and effort into out-innovating them, and this includes early transparency about vulnerabilities and a commitment to develop stronger software,” McKerchar added.
