Cryptojacking is a new type of cybercrime which does not directly affect a user’s life, but can impact their productivity and personal devices. Depending on who you talk to cryptojacking might not even be considered a cybercrime, but more of an ethical dilemma.
Defined as “the unauthorized use of a computer, tablet, mobile phone, or connected home device by cybercriminals to mine for cryptocurrency”, the process of mining cryptocurrencies involves using a computer’s processing power to solve complex math equations by running algorithms in order to “mine” the cryptocurrency.
Simply put, cybercriminals have found a way to manipulate a user’s device into mining a cryptocurrency of their choice for them. Cryptojacking has been around for close to four to five years now, but became a problem toward the end of 2017. This is in part to the fact that cryptocurrencies saw a surge in their prices at this time.
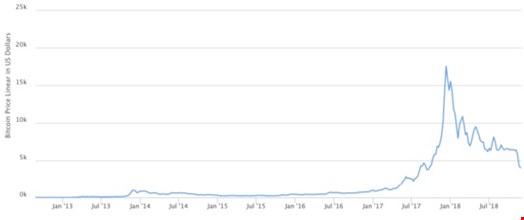
Figure 1: Price of Bitcoin from conception to end of 2018. Price surge is at the end of 2017.
This chart shows the rise and fall of bitcoin, which is the “gold standard” of crypto’s. The chart shows that at the end of 2017 and early in 2018, the price of bitcoin skyrocketed exponentially to almost $20,000 USD.
Another driving factor for the rise in cryptojacking is the fact that there is a whole lot less risk, for a much higher potential return on investment when compared to other forms of cybercrime.
Cryptojacking can be done in two different ways. One way to get a person’s device to effectively cryptojack using phishing emails where if a victim happens to “open attachments or click on links, the malware downloads onto their devices.”
The other way involves embedding malicious code onto websites through ads. If the victim is not privy to the fact that they have potentially downloaded malicious code from a phishing email, or that they visited a website with malicious code embedded on it, they could essentially be used to mine cryptocurrencies until they realize there is something wrong with their device or turn it off.
Cryptojacking through phishing occurs just like any other phishing-based attack: it is dependent on finding a user who will open an email with an attachment or link, and the user clicking on it or downloading the file. This in turn will put deliver what the attacker wants onto the user’s system.
Web browser miners reside in the code of the website, or in ads which are located on multiple websites. When a user visits this website, it will execute the code, which then runs the miner using the victims processing power to mine. Nothing is stored on the user’s computer and as soon as the user leaves the website the computers processing power is not being used by the attacker any longer.
According to a Check Point report from December of 2017, “Check Point researchers have found that crypto-miners managed to impact 55% of organizations globally.”
Cryptojacking sounds like it could be very lucrative for someone with a lot of free time on their hands. With the rise of cryptocurrency prices, an increase in price obviously means more profit if the attacker is still receiving the same amount of cryptocurrency coins from the miners. Some argue that cryptojacking is not worth the time that it takes to place malicious ads onto websites, or send phishing emails in hopes that someone clicks your link.
However, if a person was able to create a botnet and then inject the mining code onto it, the profits would be exponential. This image from Symantec details the differences that a botnet could potentially make in 30 days with file-based mining (phishing attempts), and browser-based mining (visiting websites/ads).
There is clearly a difference in the potential profits that an attacker could make using a botnet. This is due to the fact that if the attacker was able to install the malicious mining code onto the botnet systems with a file-based attack; they will be running the miners consistently. Compared to the browser-based mining method, file-based is making $700,000+ more because the browser method is dependent on the users physically being on the specific websites.

Figure 2: How Much Can a Coin-Mining Botnet Make in 30 Days?
It is important to note that the botnet in this example is comprised of 100,000 systems. This is an above average sized botnet, but is definitely not unheard of. As previously mentioned, the price of cryptocurrencies also directly correlates to the profits an attacker would bring in cryptojacking. With an operation detailed in the picture above controlling 100,000 systems running a file-based miner, the net profits could fluctuate thousands of dollars a day.
To some cryptojacking might seem like a victimless crime. This reasoning is because nothing is actually being stolen from the victim, and they aren’t necessarily being harmed. In most cases they don’t even know that their computers processing power is being used! This is not the case though. In many instances the victim is being harmed, but it is not necessarily always noticeable at first glance. According to research by Symantec, some of the affects that could be had on the end of the victim include:
- “A slowdown in device performance”
- “Overheating batteries”
- “Devices becoming unusable”
- “Reduction in productivity”
- “Increased costs due to increased electricity usage, and for businesses operating in the cloud that are billed based on CPU usage”
So how can a user avoid cryptojacking and avoid the annoyance of a slower system, unusable devices, and overheating batteries all at the expense of an attacker getting “free” money? A good place to start is to install a security software suite. Any suite worth its salt will prevent cryptojacking scripts.
A purpose-built solution such as an ad-blocker, and there are also anti-crypto mining extensions such as “no coin” and “miner block”.
Just as important is that awareness about cryptojacking must be spread. With the rise of cryptocurrencies, and the lack of risk involved in this kind of online threat, cryptojacking is only going to become more prominent. A First Look at Browser-Based Cryptojacking suggests that browser developers themselves could help mitigate this issue by “throttling client-side scripting, warning users when client-side scripting consumes excessive resources, and blocking the sources of known cryptojacking scripts.”
While many consider cryptojacking a crime, there are some who see otherwise. However, there is unquestionably an ethical dilemma when it comes to cryptojacking users. In-browser mining is a concept that is similar to cryptojacking. The difference lies in consent. There are some websites where users will agree to use the website if the site is allowed to run a crypto miner script. In theory this could be a substitute for ad-revenue if it were profitable enough.
Cryptojacking happens unbeknownst to the user, and can leave them frustrated with the issues that can come along with the use of their processing power without their knowledge. For many, the decision to allow a website to use your processing power while browsing their site could be a fair trade off as long as they don’t require too much processing power to noticeably slow down your system. It is simply the ability to make an informed decision that makes the difference ethically, and criminally, between cryptojacking and in-browser mining.
Christian Eaddy is currently a student at East Carolina University, studying Information and Computer Technology with a concentration in Security.
