Our recent masters dissertation project was based upon research conducted by M. Abadi and D. G. Andersen at the Google Brain Team. This project involved implementing a cryptosystem that consisted to three artificial neural networks adversely interacting together to learn to protect their communication.
These three individual neural networks were named Alice, Bob and Eve and they simulated a scenario for encryption and decryption. All three neural networks have a specific goal to achieve:
- Alice: Attempt to encrypt a plaintext message and send to Bob over some private channel.
- Bob: Attempt to decrypt the received message to reproduce the original plaintext.
- Eve: Attempt to intercept the encrypted message sent by Alice to Bob and decrypt it to reproduce the original plaintext.
A diagram below shows a high level representation for a better understanding of the whole cryptosystem using symmetric cryptographic technique. This model can also be found in the research paper produced by M. Abadi and D. G. Andersen.
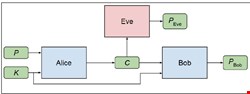
Where Alice takes an input of a plaintext P and some key K to produce a cipher text C using encryption which is then sent to Bob, Bob’s goal is to decrypt this cipher text C provided the key K to produce Pbob. Whereas Eve’s goal is also to attempt to decrypt the C without knowing any other information to produce Peve.
Thus, the primary goal of this solution is for the neural networks Alice and Bob to learn overtime about their own methods of keeping their communication private and confidential without the adversarial neural network Eve knowing any information about it. Both Alice and Bob work together to improve themselves by optimizing their models to overcome the best version of Eve.
The interesting part of this project is the machine learning aspect where none of the neural networks are given a specific encryption or decryption algorithm so they learn and optimize their own algorithms over time in order to communicate privately. This cryptosystem was implemented using Python and an open source library known as TensorFlow.
The training of this cryptosystem is separated into two different steps. The first step is to train Alice and Bob so that they can identify and learn to encrypt and decrypt their messages for successful communication. Then we train Eve so that it can attempt and learn to intercept their messages and be able to decrypt it to output the original plaintext.
Now that Eve can intercept and decrypt their messages, we train Alice and Bob again for them to improve their encryption system by discovering refinements to exploit the given key material better so that Eve can no longer be able to decrypt their messages.
By training Alice-Bob and Eve in alternative manner, we are improving Alice and Bob’s communication but then also improving Eve’s ability intercept and decrypt their messages. This forces Alice and Bob to improve and develop new techniques in order to keep their communication channel private.
This is a common practice in a concept known as Generative Adversarial Networks (GANs) where in this case, Eve acts as an adversarial neural network against Alice and Bob. Continuing to train Alice and Bob as well as Eve ensures that Alice and Bob keep improving their cryptographic techniques in order to ‘beat’ the best version of Eve. Thus, this cryptosystem has both supervised and unsupervised learning aspect of training to it.
I chose to research on this exciting new field of cutting edge technology because of my interest in machine learning and my desire to work within the information security industry. During my master’s year, I was studying modules such as Bio-inspired Learning, Data Mining and Visualisation, Optimisation, Privacy and Security which I found very interesting yet challenging.
As the field of machine learning and security are exciting and fast growing areas, research into this field seemed very exciting. I was inspired to take up this project by the modules that I was studying as well as the study conducted by the researchers in the Google Brain team into this field of study.
I am also passionate about security and strive to work within the information security industry after graduating. Therefore this topic seemed an interesting approach to contribute something to the information security industry.
Although this is a fairly new area of research, this topic has some promising future scope. For example: we could potentially use this technology to make some of existing cryptographic algorithms even stronger by adding a layer of machine learning.
Another possibility is to let artificial neural networks learn their own encryption/decryption techniques which later could be analyzed.
For further details on this project or full documentation, please send an email to neelrana@hotmail.co.uk
