Ransomware is a relatively new malware type that attempts to encrypt a compromised device’s data using a strong cryptographic algorithm. To recover the data, the victim will have to pay a ransom (usually using Bitcoins) to obtain the password or decryption key.
While there have been significant efforts in preventing ransomware from infecting a machine (i.e. using anti-virus products) or in limiting their damage (i.e. through sandboxing), the recent WannaCry attack has demonstrated that there are many vulnerable devices that cannot be upgraded to new technologies, and that there are many inattentive users who still run executables received from unknown sources, bypassing the available security protections on a machine.
Therefore, we need a plan for Doomsday and the worst case scenario: if a ransomware has been successfully launched on a system, can we detect that this has happened while it is still happening, and therefore while it is still possible to reduce the damage being caused?
Machine learning technologies have always been used as a tool for cyber-threat detection. However, as any machine learning-based detection algorithms must rely on measuring some features (system characteristics) that are characteristic of an infection, bypassing a machine learning-based threat detection mechanism depends on how easy it is to infect a target device without changing the features that are being measured.
David Bianco’s Pyramid of Pain may serve as a guide to find the best features for a machine learning-based threat detection algorithm: to make it tough for the attacker we need to concentrate on measuring features that best reflect attackers’ Tactics, Techniques and Procedures (TTPs).
We propose that changes in the energy consumption patterns of an infected device can be used as such a feature for ransomware detection. It could be trivial for a malware developer to change a malware’s function calls or its behavior, but changing its power usage pattern is less likely and is more difficult to realise.
Additionally, power usage patterns are relatively similar on different platforms. Power consumption flow graphs of the Simplocker Ransomware and of the Facebook Application are shown in these graphs, and these may demonstrate significant differences between the power usage patterns of a normal application and of ransomware. Therefore, power consumption-based detection methods appear to be a viable approach.
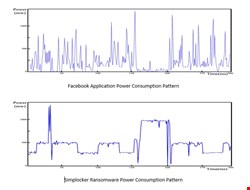
To develop a fingerprint of energy consumption, initially, we recorded power usage of Gmail, Facebook, Google Chrome, YouTube, WhatsApp, Skype, Angry Birds, Google Maps, Twitter, Instagram and five ransomware samples with active Command and Control (C2) at the time of experiment on three different Android devices, namely: a Samsung Galaxy SIII (Android 4.4), a Samsung Galaxy S Duos (Android 4.0.1), and an Asus Padfone Infinity (Android 4.4).
We applied four state-of-the-art machine learning classification algorithms, namely: k-Nearest Neighbor (KNN), Neural Network (NN), Support Vector Machine (SVM) and Random Forest (RF), on the power usage samples to recognize the class of each sequence of power consumption. As shown in this table, the best accuracy of 83.7% was achieved using KNN (in a 30 second time frame).
Table 2: Accuracy of Different Machine Learning Algorithms for Power Consumption Based ransomware detection
|
Machine Learning Algorithm |
Accuracy |
|
KNN(K=1 & DTW*) |
83.70% |
|
Neural Network |
75.93% |
|
Random Forest |
80.74% |
|
SVM |
78.52% |
*DTW: Dynamic Time Wrapping
While these results may indicate the suitability of KNN for our purpose, an accuracy of less than 90% may limit its suitability for mass deployment. Moreover, making small changes to the flow of power consumption that are sufficient to reduce this accuracy further would not be a difficult task for a particularly dedicated adversary. Therefore, we have devised an algorithm to grind power consumption flow and to create sub-samples of power usage which best reflect a pattern of power usage to distinguishing a ransomware from a benign application, as shown below:
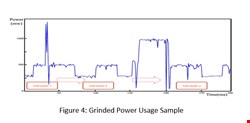
While the flow of power usage pattern may not, by itself, be a good enough feature for ransomware detection, grinding power usage to parts that best reflect differences between a goodware and a malware power consumption may be more promising. Changing the pattern of power consumption of an application at this level of detail is a much more difficult task compared to changing its overall power consumption flow as described above.
We built an algorithm that creates best sub-samples within a given power usage flow to differentiate between a ransomware and a goodware. Using the grinded pattern of power usage instead of its flow significantly increased accuracy of detecting running ransomware using the KNN technique, to a level suitable for practical and real-world implementations. As shown above, more than 90% of ransomware are detected within five seconds of their launch and more than 92% are detected within the first ten seconds.

Mobile devices have much noisier power consumption patterns compared to Internet of Things devices. While we could achieve a high accuracy in mobile (Android) ransomware detection, our approach may provide an even more promising solution for ransomware and malware detection on future IoT devices.
We believe the area of active threat hunting against live targets, which is looking at detection of threat actors based on the assumption of successful launch of their threat vectors, is an important and growing area of development in the cybersecurity domain. It is always necessary to have a plan for Doomsday!
Andrew Young hase worked in industry (Rolls Royce, Logica) on projects for the Ministry of Defence and the European Space Agency. He also worked as a freelance independent, working on programming projects for UK Trading Standards, and on security management projects for Technology Appraisals.
Within the University sector, he worked as a contract researcher at UCL and Salford on projects on X.500/LDAP/SMTP security and public key infrastructures
Ali Dehghantanha is a Marie-Curie International Incoming Fellow in Cyber Forensics and a fellow of the UK Higher Education Academy (HEA). He has served for many years in a variety of research and industrial positions. Other than Ph.D. in Cyber Security he holds many professional certificates such as GXPN, GREM, CISM, CISSP, and CCFP. He has served as an expert witness, cyber forensics analysts and malware researcher with leading players in Cyber-Security and E-Commerce.
Kim-Kwang Raymond Choo (SM'15) received the Ph.D. in Information Security in 2006 from Queensland University of Technology, Australia. He currently holds the Cloud Technology Endowed Professorship at The University of Texas at San Antonio, and is an associate professor at University of South Australia, and a guest professor at China University of Geosciences, Wuhan. He is the recipient of various awards including ESORICS 2015 Best Paper Award, Winning Team of the Germany's University of Erlangen-Nuremberg (FAU) Digital Forensics Research Challenge 2015, and 2014 Highly Commended Award by the Australia New Zealand Policing Advisory Agency, Fulbright Scholarship in 2009, 2008 Australia Day Achievement Medallion, and British Computer Society's Wilkes Award in 2008. He is a Fellow of the Australian Computer Society.