Ransomware is again making headlines following the WannaCry and NotPetya attacks earlier this year. This new strain, dubbed ‘Bad Rabbit,’ appears to have spread quickly through networks with infections reported in a number of regions.
While the virus appears to have started infecting systems this week [Tuesday October 24 2017], our research indicates that the group behind the attacks spent considerable time creating an ‘infection-network’ as activity appears to date back to at least July, with the majority of sites relating to media and news.
An Adobe Costume
The virus is disguised as an Adobe Flash installer, which pops up on the user’s screen, when they visit what they believe is a legitimate site. Given that the attackers are targeting media and news sites, that have previously employed Flash to enhance the visitor experience, this request to download an update may not immediately arouse suspicion. If the user follows the redirection the attack begins and the ransomware dropper downloads.
As soon as the victim executes the dropper, for which admin privilege is needed, a malicious DLL named infpub.dat is saved and is then run using the usual utility rundll32. Then, the infpub.dat file tries to brute-force NTLM, a Microsoft authentication protocol, login credentials and download an executable dispci.exe, which appears to be derived from the well-known utility DiskCryptor code - a disk encryption module. The execution of the last file downloaded begins the encryption phase and the replacement of the bootloader as already seen in previous NotPetya attacks.
However, Bad Rabbit doesn’t cause a random diffusion from a single point of failure, which incidentally means the domain name used as a kill-switch in the WannaCry scenario does not apply. Instead, the virus appears to affect websites that seem to relate to the states in which the attackers wanted to spread the malware.
The time attackers have invested in the creation of their infection-network is typically crucial, particularly if they planned to execute an attack with specific targets while retaining anonymity as to the identity and/or origin of the group.
However, one saving grace is that Bad Rabbit is not installed automatically, which means that the attacker is reliant on users clicking on the malware to deploy the malicious code. This suggests a lack of preparation, and even ignorance of how ransomware attacks work, on the part of the assailants.
That said, it is important to recognize that employees can inadvertently become the weakest point in an organization when it comes to cybersecurity as all too often they are not aware of the threats faced nor the tactics attackers will use to dupe them.
Not new but very effective
Extortion through ransomware attacks is one of the oldest tricks in the hacker’s book, and even though organizations have adopted various protection mechanisms, these attacks remain successful.
Bad Rabbit is an example of how a small variant of vector attack, delivery method, etc., is enough to have similar effects comparable to previous scenarios (i.e. NotPetya, WannaCry, etc.)
The reality is that we will continue to see more of this kind of attack, given that it does not require the development of complex exploits, but simply the combination of open-source code that can be found by anyone.
It’s crucial that organizations understand the bigger role employees play in securing company’s systems and data and start training them to recognize when something online looks suspicious. In addition, organizations need tools that will help them immediately identify when something ambiguous is happening within the infrastructure.
Applying artificial intelligence and machine learning for real-time detection and response, organizations can monitor for malware to rapidly discover and act to remove malicious code and the risks posed before harm is done.
Prevention is always better than cure as, if infected, it is never advisable to pay the ransom as it is not guaranteed that the criminals will honor the agreement and restore systems/data.
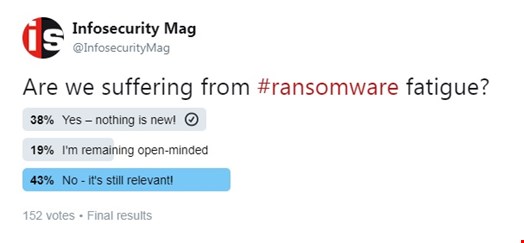
Infosecurity asked our Twitter audience on whether the cybersecurity industry is suffering from ransomware fatigue. We collected votes from 152 users, and the results show that despite the three major variants we've seen in 2017, this should continue to be taken seriously.