
In this challenging economy, businesses and organizations often can’t allocate enough scarce financial resources to adequately protect critical IT infrastructure. Yet, the cybercrime threat has never been higher. Some service providers are reporting up to 100,000 potentially new malware samples each day, many of these targeted against high-profile organizations.
And the malware threat keeps growing. As was most recently in the news, hostile governments may use attacks to seek information on anything from human rights activists to the location of strategic assets, such as potential oil fields. More commonly, attackers are enterprising criminals seeking to steal organizational resources, property or valuable private information, such as credit card or Social Security numbers.
As malware and cybercrime reports continue to dominate the news, it is safe to say that no company, government agency or other organization remains unscathed when confronting this daily malicious swarm. Organizations must also be concerned with the far-reaching threat to goodwill of such information breaches. Customers, partners, and other company stakeholders can quickly lose confidence in organizations that are not able to secure their information.
When organizations come under such malicious attacks, they must be able to respond quickly. The magnitude of losses usually increases with delays in response and mitigation. Outsourcing analysis of threats to third-party experts often causes significant delay and, in many cases, third parties are able to identify whether suspicious pieces of code are in fact malicious, but they may be unable to provide a comprehensive forensic report of the attack as it occurred inside the compromised organization. Internal analysis teams eliminate costly bottlenecks and ensure analysis discoveries are complete.
Third-party analysis is not an option for organizations with sensitive or classified information because attack information cannot be externally transferred. Compounding the problem, these organizations are among the most frequent victims of targeted attacks. Malware authors can potentially gain high rewards from these attacks, and therefore put significant effort into ensuring its success.
Targeted threats will often contain the latest and most complex social engineering and exploit techniques for stealthily penetrating an organization. When the attack is discovered, analysts may encounter heavily protected and obfuscated code, complicated by technologies such as rootkits and advanced packers that mask intent.
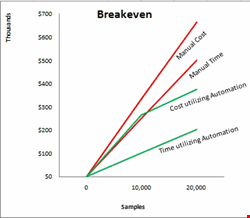
When responding to attacks, organizations must determine to what degree they have been compromised. This includes determining what data has been accessed, who initiated the attack, who accessed the data, and who may be in possession of that data. These tasks quickly become daunting in large organizations facing tens of thousands of samples of malicious code and needing up to 20 minutes per sample for analysis using manual reverse engineering methods. This is enough time to bring down a network and compromise a significant amount of data. Once the analysis phase has been completed, actions to clean up, minimize effects, and prevent future attacks must be undertaken.
With limited expertise and the high cost of employing threat analysts who use manual debugging and research methods, organizations need more efficient solutions.
To address these challenges, larger enterprises and security-conscious government agencies employ highly trained, dedicated security analysts who combine commercial and home-grown applications to reveal the objectives of specific malicious threats. These analysts are a precious resource: in high demand and, because of high levels of education and experience, often relatively expensive to hire and retain.
There are some commercial products, however, that offer automated approaches to high-volume malware analysis and the potential for dramatic improvements in ROI.
Years of testing in security analysis labs by industry leaders has resulted in sandbox-based behavioral systems, the understanding of tactics used by attackers, fingerprinting of code, generic detections, reputation technologies and other methods that effectively and quickly automate responses to new threats. Response times can drop from days to hours, minutes and even seconds as analysts effectively address attacks in a day-zero context, rather than days, weeks or months.
Sandbox technologies deliver on cost-effectiveness and timeliness claims by doing high-volume malware analysis in a safe environment. They usually simulate or virtualize a Windows-based computer environment or use various virtual machine technologies. Inside the sandbox environment, the file will usually behave as it would in a real computer system under attack, giving the organization a quick overview of malicious capabilities.
Different approaches boast different benefits. Truly emulated systems simulate the entire computer environment, including the hardware, operating system, software and network services. Like a video game, nothing physically happens in the real world as a result of malicious actions. Benefits offered by emulation usually include faster analysis, a more effective defense against the cybercriminals identifying the system as a malware-detection tool, and safety against malware breakouts from the environment.
Virtual machine-based technologies are more prone to exploitations, but offer greater flexibility for custom and third-party software installation and operating system version and patch levels. Hybrid solutions use some emulation while virtualizing other functions using resources from the host system to reap some benefits of both approaches.
Going forward, advances are being pioneered in reverse engineering and forensic technologies to address rapidly emerging new threats and exploits. Although current solutions on the market may not be silver bullets to the ever-growing problem with malware, they can quickly improve and speed up response at a fraction of the costs of traditional methods.
Matt Allen is a technology and forensic analyst with Norman Data Defense Systems and has backgrounds in computers, information sciences and business. He has worked in different roles at Norman over the past eight years, including incident response, software development and marketing. Allen currently works primarily with the SandBox & Technology team.