While there is absolutely no question that a multi-layered information security solution is required to protect one’s business, it is very easy for organisations to get caught up in the hype of all the latest and greatest technologies promoted by information security vendors charged with combating the nastiest and sneakiest of attacks – the information security technologies that have been tried and true for decades are being left to stagnate by information security vendors across the industry.
This isn’t because the information security technologies don’t work well as a method of protection – it’s because they don’t make information security companies as much money as their shareholders require and therefore the investments in these areas typically fall off..
This lack of focus on core information security solutions does a number of things that businesses should be concerned with. Here are my top three:
- A lack of continued focus on core information security solutions such as a host intrusion prevention system (HIPS) and behavioural-based malicious code detection opens the door to new information security threats that can find new ways to skirt protection and leverage the user, applications, and networks to their benefit.
- The removal of key technologies – such as a desktop firewall – is a clear sign that a number of information security vendors are taking the easy road for their product development teams – at the expense of their customers’ protection.
- We also find that some information security vendors are using the tried-and-true solutions purely as a checkmark item, not really improving them, leveraging them only to say they have them, and to help shore up the new technologies that are being acquired.
It is certainly easy to hypothesise – but what does this really mean? Let’s take a couple of information security threat categories that have also been around for a while; keyloggers and buffer overflows. There hasn’t been a lot of press around these two categories in a while. This does not mean they have disappeared or have been blocked, I would suggest that they have in fact gone back to the basics themselves – only taking the time to improve upon what they do best.
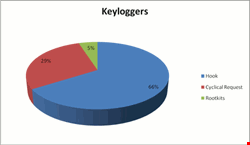
Keyloggers
There are two primary types of keyloggers: Hardware keyloggers and software keyloggers.
Hardware keyloggers can record keystrokes from the user’s keyboard and send the information back to the controlling computer. Software alone cannot detect or block this. Fortunately, physical access to the machine is required.
Software keyloggers, on the other hand, are software applications designed to record keystrokes and also intercept mouse events and perform screen logging through one of three methods:
- Hook: The main interception of keyboard events
- Cyclical request: The application requests events from the keyboard
- Filter driver: Located in a RootKit, it is a driver installed in the kernel of the operating system. These components require administrative privilege in order to install itself on the target system.
95% of the keyloggers run at the user level, bypassing the need to gain administrative privilege in order to be installed and to function. The challenge for businesses given this method is that their signature-only protections and their stagnant rule-based host intrusion prevention technologies and their end-of-life desktop firewall applications – even when combined in a single bundle – will have a difficult time keeping up with what the keyloggers are throwing at them.
Buffer overflows
Buffer overflows are essentially a flaw in a software application that is provoked by sending more data than a buffer can contain. This overflow of information allows code injections into the application being attacked, allowing the injected code to execute when a specific event occurs. The compromised application – or even a remote system connecting through the compromised application – can take complete control of the affected machine.
With more than 85% of software vulnerabilities classified as memory overflows, they fall into one of three categories:
- Stack overflow: An overflow in the call stack, a static area of memory used by programmes to perform their functions.
- Heap Overflow: An overflow in the dynamic memory area of an application.
- Return-To-Libc: A buffer overflow launched through a pre-existing function located within the target application being attacked.
Worms using buffer overflow
These top worms all share something in common; a vulnerability in the Microsoft Windows operating system with new techniques for spreading themselves.
|
Worm
|
SQL Slammer
|
Blaster + Sasser
|
Conficker
|
|
Vulnerability
|
MS02-039
Buffer Overflow on SQL 2000 ……
24 Jul, 2002
|
MS04-011
Buffer Overflow in LSASS Service of Windows.
13 Apr, 2004
|
MS08-067
Buffer Overflow in Server Service of Windows.
23 Oct, 2008
|
|
Discovered
|
25 Jan, 2003
|
30 Apr, 2004
|
21 Nov , 2008
|
|
Method of Transmission
|
Generates a random public IP and tries to attack each of them
|
Attacks workstations using network ranges and emails
|
Updates and encrypts itself thru HTTP Pull
Utilised network shares and removable devices
|
All of have a buffer overflow as their primary entry point. What makes them different is their new methods of propagation.
It may seem obvious that after Blaster and Sasser worms, we should have protections in place to prevent worms of this nature from spreading through memory or via buffer overflows. The self-update and built-in encryption of Conficker, however, shows that worm detections that rely on signatures or rule databases alone won’t cut it
Concluding remarks
Something you might want to consider as each of your information security technologies comes up for renewal – take the time to do a proof of concept, and test the core technologies against some of the new threats and compare information security offerings against each other.
Again, while it is important to move with the times and to stay in tune with the somewhat newer technologies such as full-disk encryption, file-based encryption, device control, application control, and network access control – it is important not to lose sight of the technologies you’ve already made an investment in and have relied upon for years.
Seems pretty basic, doesn’t it?
Author’s Note: |
| Fayçal Daïra, is the chief technology officer for SkyRecon Systems of San Jose, California, USA and Paris, France. Contact him at fdaira@skyrecon.com. |