
The near-ubiquitous proliferation of WiFi in recent years has increased exposure to wireless security threats happening over WiFi links, and certain requirements mentioned in the PCI Data Security Standard (DSS) version 1.2 document have either implicit or explicit implications for security of the cardholder data environment (CDE) from wireless threats. These requirements, clubbed together, are now being termed as PCI wireless requirements.
In order to understand the scope of the requirements and guide organizations with compliance, PCI also released a set of wireless guidelines in July 2009. An organization/merchant seeking PCI compliance should ensure that these requirements are fulfilled at all sites comprising the CDE, irrespective of whether a wireless local area network (WLAN) is deployed inside the CDE or not.
These requirements are basically aimed toward protecting sensitive cardholder data from thefts via the exploitation of possible WiFi vulnerabilities at a merchant’s site. After successfully meeting these requirements, an organization/merchant is generally said to be PCI wireless compliant. If a merchant fails to comply with the guidelines, then it will bear the costs, which can be significant when the first PCI DSS compliance deadline approaches this September.
Also, failure to comply with these standards will leave organizations prone to wireless threats that can result in theft of sensitive card holder information, thereby triggering potential litigation, brand damages, and disruption of business. Because some merchants have already experienced major wireless data breaches causing huge financial losses, many are looking for various methods that achieve compliance and secure its CDEs from wireless threats.
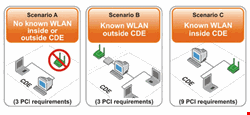
On the basis of WLAN deployment at a merchant’s site, the CDE can comprise the following:
- No WLAN inside/outside the CDE – Means that no WLAN is deployed at a particular site.
- Known WLAN outside the CDE – WLAN is deployed outside the CDE at a merchant’s site for reasons such as inventory management, guest access, etc. This type of WLAN resides on an isolated network other than the CDE network.
- Known WLAN inside the CDE – WLAN is deployed as the part of the CDE network. The WLAN may or may not be used for processing of cardholder data.
As described in the PCI wireless guideline document, there are several universal wireless requirements that must be fulfilled for all types of CDEs; there are also other additional requirements, but these need to be fulfilled primarily for sites with a known WLAN inside the CDE to achieve PCI wireless compliance for a particular site.
Universal requirements aim at scanning all merchant sites – at least quarterly – for presence of unauthorized/unmanaged WLANs, such as rogue access points (APs), ad-hoc connections, soft APs, etc. After the scan is completed, these unauthorized WLANS must be eliminated. Additional requirements include changing default wireless settings, monitoring/alerting wireless intrusion, using strong wireless encryption, logging wireless activity, physical restriction for authorized wireless devices, and development and enforcement of wireless usage policies.
PCI has recommended the use of handheld wireless analyzers such as Netstumbler and Kismet for achieving universal requirements, and the use of wireless IDS/IPS solutions capable of handling all wireless requirements. However, both of these stipulations create problems for merchants. The relative discomfort comes from the following:
- Using wireless analyzers is a manual method requiring dedicated personnel walking around the site with a device to collect relevant information. Hence, it is time consuming and tedious, especially if performed at many sites.
- Data collected from analyzers needs to be manually interpreted for unauthorized WLANs, increasing the probability of errors.
- A regular schedule for wireless scanner surveys must be created. Delays can lead to non-compliance.
- Use of wireless analyzers is limited, mainly, to the fulfillment of universal requirements. It is not practical to use these analyzers 24/7, and therfore wireless threats occurring outside of regularly scheduled scan times will go undetected, resulting in possible compromising of the CDE.
- A PCI-oriented IDS/IPS solution helps merchants achieve automatic compliance, however, most of these solutions are very costly and complex for small and medium-sized businesses.
- An IDS/IPS solution requires dedicated IT support for installation, maintenance, and monitoring.
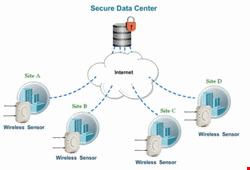
Observing the aforementioned problems and understanding the paint points of recommended methods, some vendors have recently launched SaaS (software-as-a-service) offerings for PCI wireless compliance. These solutions generally consist of setting up wireless sensor(s) at an appropriate on-site location and ensuring its connectivity with the vendor’s data center. Merchants can benefit in several ways from SaaS PCI wireless compliance products:
Automated and sustained compliance: SaaS offerings provide automated and sustained compliance for PCI wireless requirements, eliminating worries about arranging IT support or personnel for carrying out walk-around wireless analysis. Automated compliance is advocated by many consultants around the world for its competitive business advantages.
Affordable cost: SaaS solutions are generally subscription based and require a monthly fee, which is affordable for most of merchants. These companies benefit from automated compliance without having to pay hefty upfront amounts for a wireless IPS/IDS solution.
Availability of various plans: Some SaaS vendors have launched flexible plans to suit merchants’ CDE needs at a specific site. Plan charges vary based on features and can be tailored for specific security features on request.
Easy implementation and scalability: Requires only basic configuration details and installation of a sensor at the site. In addition, SaaS products can be easily extended to a new site.
Low overhead: Overhead costs, such as dedicated IT support and maintainence, are avoided with SaaS offerings, all of which the merchant would need to bear if it opts for wireless analyzers or a WIPS/WIDS solution.
Easy upgrade to other plans/full-scale WIPS: Some vendors provide subscribers easy upgrades to higher-level PCI compliance plans (with additional features) or to a full-scale WIPS solution.
24/7 threat visibility: Because wireless sensors are constantly scanning in a SaaS arrangement, the data center will continuously analyze your scan data for possible wireless threats.
SaaS options offer relief to merchants of all sizes through automated and cost-effective compliance for PCI wireless requirements. Moreover, security-conscience companies can subscribe to advanced PCI SaaS plans for cost-effective, automatic, and continuous detection and prevention of wireless threats.
Experience in detection and prevention of all possible wireless threats are key considerations when choosing the appropriate system. Other merchants must ensure reasonable additional costs. Another consideration is quality, because a cheap offering can result in non-compliance and a CDE vulnerable to Wi-Fi hackers. The vendor landscape is surely going to increase for such offerings, so organizations should choose the one that best suits their needs.
Ajay Kumar Gupta is the acting tech lead, engineering, at AirTight Networks, a global provider of enterprise WiFi security and performance management products. He is a frequent contributor to some leading security magazines and AirTight’s blog.