
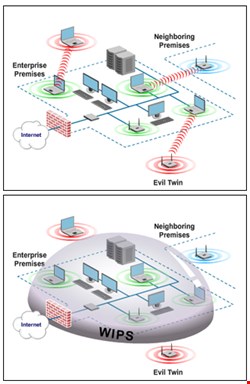
Corporate Wi-Fi clients within their business premises often connect to unauthorized Wi-Fi networks. In Wi-Fi security jargon this is called a Wi-Fi client mis-association vulnerability. The unauthorized Wi-Fi network, in general, is neither approved nor managed by the network administrator of the corporate Wi-Fi clients; it often belongs to neighboring establishments. In some cases, it may be set up in the neighborhood with malicious intent to victimize corporate WiFi clients (known as WiPhishing or Evil Twin).
Mis-association, if undetected and uncontained, can compromise employees’ Wi-Fi devices, such as laptops/netbooks, PDAs and smart phones. Also, in cases such as bridging between the Wi-Fi client and a corporate wired network, mis-association can result in unauthorized access to the network. All totaled, this can result in theft of company’s or employees’ confidential data and/or disruption of corporate network services.
Following are the some of the most common reasons that cause Wi-Fi client mis-associations. Some of these findings are supported by extensive scan studies, such as the Airport Scan Study and Financial Districts Scanning Report, which were recently published to explore Wi-Fi related vulnerabilities in various business verticals.
- Insufficient Coverage of Corporate Wi-Fi/No Wi-Fi Policy: Planning Wi-Fi coverage that will please all employees has always been a challenge. This often leads to unavailability of a Wi-Fi network for some corporate clients. Automatic mis-association occurs when the Wi-Fi client automatically connects to an available but unauthorized Wi-Fi network with a stronger signal than that of the corporate Wi-Fi network. Manual mis-association arises when a user – out of frustration with weak/non-existent corporate Wi-Fi signals – deliberately connects to an unauthorized Wi-Fi network (hotspot, municipal Wi-Fi, etc.) that is visible in the airspace of the physical location. Some corporations have a no-Wi-Fi policy on office premises due to wireless security concerns. Ironically, however, such a policy creates stimulus for corporate Wi-Fi clients to effect mis-association with neighboring Wi-Fi networks while on company property.
- Restrictions on Use of Internet in the Office: Many corporations restrict use of the Internet to minimize distractions and increase productivity of its employees, as well as to prevent malware from entering the corporate network. Such a policy is often enforced via a corporate firewall. However, this policy often tempts employees to deliberately connect to unauthorized Wi-Fi networks in order to gain full-blown Internet access.
- Presence of Prevalent SSIDs in Client’s Preferred Network List: Prevalent SSIDs – such as default SSIDs, hotspot SSIDs or SSIDs for municipal access – are often present in employees’ Wi-Fi preferred network list (PNL). This happens because of the typical behavior of popular Wi-Fi drivers, such as Windows, which cache earlier connected SSIDs and later automatically seek a connection to them. Corporate Wi-Fi clients in these cases can unwittingly connect to an unauthorized Wi-Fi network in the area with an SSID that matches one in the PNL.
- Malicious Activity in Your Area: It is also possible for hackers to set up unauthorized Wi-Fi in the vicinity of your facility (parking lot, street, neighboring building, etc.) and lure corporate Wi-Fi clients to connect with an unauthorized Wi-Fi network. Once connected, a suite of attacks can be launched on the victim client. This activity is called WiPhishing, Evil Twin, Honeypot, and so on. Many software tools – such as KARMA, delegated, hotspoter – are also freely available to set up these types of unauthorized Wi-Fi networks.
- Ad-hoc Connections: Ad-hoc connections (peer-to-peer connections between Wi-Fi clients) cannot be managed by the administrator and, therefore, are inherently vulnerable. Thus, any corporate Wi-Fi client that becomes part of an ad-hoc network is considered mis-associated. Ad-hoc connections are vulnerable to eavesdropping and data theft because they fail to exercise proper wireless security controls. Corporate Wi-Fi clients that are vulnerable to forming ad-hoc connections (because of ad-hoc permitted Wi-Fi settings) can also be exploited over Wi-Fi by deliberate hackers from outside the premises. A hacker can build layer-2 Wi-Fi ad-hoc connections with corporate devices and launch a suite of attacks.
Detection and active prevention of mis-associations, occurring due to any combination of the described reasons, is one of the most critical requirements for administrators to ensure security of network infrastructure and authorized Wi-Fi devices on company property. The most robust way of doing this is to have another layer of security infrastructure, widely known as a wireless intrusion prevention system (WIPS), over the corporate Wi-Fi infrastructure.
A complete and well-built WIPS solution actively monitors and blocks all mis-association threats and keeps corporate Wi-Fi clients pinned down to authorized networks. And the best part is that the administrator does not have to intervene because the WIPS will do the job of containing mis-associations.
Ajay Kumar Gupta is currently acting as tech lead, engineering, for AirTight Networks, a global leader in enterprise Wi-Fi security products. He is a frequent contributor to some leading security magazines and AirTight’s blog. For more information he can be reached at ajaygupta.hbti@gmail.com.