The thought of software vulnerabilities in pacemakers and other medical devices and systems is troubling, particularly in light of recent (and preventable) attacks from ransomware such as WannaCry and Petya. The possibility of your pacemaker being hacked is frightening enough, but if a critical medical device you depended on were being held for ransom, what would you pay to unlock it?
Is that a real risk? It’s certainly a possibility. Implanted devices have been around for decades to allow doctors to collect vital patient data, but many of these devices were distributed without any type of encryption or defensive mechanisms in place. Security researcher Barnaby Jack once demonstrated a system that could compromise insulin pumps that communicate wirelessly, and was planning to demonstrate a remote hack on pacemakers before his untimely death in 2013.
Use of Open Source in Medical Devices
Secure software is an ephemeral concept. What we think of as secure today can change overnight as new vulnerabilities are discovered and disclosed. As code ages, the probability is high that more vulnerabilities are likely to be disclosed. Black Duck’s 2017 Open Source Security and Risk Analysis (OSSRA) research found that the average commercial application included almost 150 discrete open source components, and that 67% of over 1000 commercial applications scanned included vulnerable open source components.
For their own research on pacemakers, Billy Rios and Jonathan Butts acquired hardware and supporting software for four different brands and looked for weaknesses in architecture and execution. One of the biggest issues noted in the paper they published earlier this year was one we see time and again — unpatched software libraries.
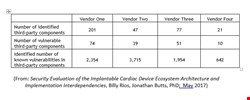
All four pacemakers examined contained open source components with vulnerabilities, and roughly 50% of all components included vulnerabilities. Most shockingly, the pacemakers had an average of 50 vulnerabilities per vulnerable component and over 2,000 vulnerabilities per vendor.
The researchers wisely did not disclose which pacemakers they acquired, and did pass on the information to the Department of Homeland Security so the manufacturers of the tested devices could address the flaws. We don’t know how old the devices and software were, but, since the equipment was purchased on eBay, we can assume they were not newer models. As I noted earlier, older code—whether proprietary or open source—is more likely to have had more vulnerabilities disclosed.
Their paper also doesn’t state if the researchers checked for software/firmware updates from the vendors prior to analysis. My assumption is that they did not, but whether this would have made a real-world difference is arguable.
Black Duck’s own research indicates that vendors are typically unaware of all of the open source they use, since it can enter the code base in so many ways. On average, prior to having a Black Duck code scan, our customers were aware of less than half of the third-party libraries they use.
What should manufacturers of medical devices do?
The problem here isn’t the use of open source. It’s the fact that open source is often invisible to the organization using it. Open source use is pervasive across every industry, including the medical device industry.
When it comes to software, every manufacturer wants to spend less time on components connecting various pieces together and focus on unique features that will differentiate their device from the competition. The open source model supports that objective by expediting agile product development.
Yet open source vulnerabilities may open up users to targeted or non-targeted attacks. Depending on the software (home monitoring, physician, programmer, etc.), the attack could affect a single patient or an entire practice. The potential for monetary gain is very real; the healthcare provider in an attack may have to choose between a ransom and the welfare of its patients.
When the WannaCry ransomware spread across the world, multiple UK hospitals reported that their radiology departments were completely knocked out by the ransomware outbreak. If the attack is on implantable medical devices, this could become a life or death decision.
Unless organizations in the medical device supply chain carefully track the open source they use, and map that open source to the thousands of vulnerabilities disclosed every year (though still less than that reported in commercial code), they will be unable to protect their applications—and their customers—from those vulnerabilities.
Medical device manufacturers and their suppliers should adopt management practices that can inventory open source software; that maps software against known vulnerabilities as well as alerting to new security threats; that identifies potential licensing and code quality risks; and that can maximize the benefits of open source while effectively managing risks.
