Mid-pandemic cybercrime volume may or may not be increasing, but it is pivoting. To address it, businesses not only need to secure home offices and remote access, they must also develop a better cloud security strategy.
Phishing the Pandemic
Phishing, malware and ransomware distribution are using coronavirus as a lure. Cyber-criminals are registering malicious domains using coronavirus-related keywords. Worst of all, even more sophisticated attacks can be expected against new or hastily deployed work from home infrastructure and services.
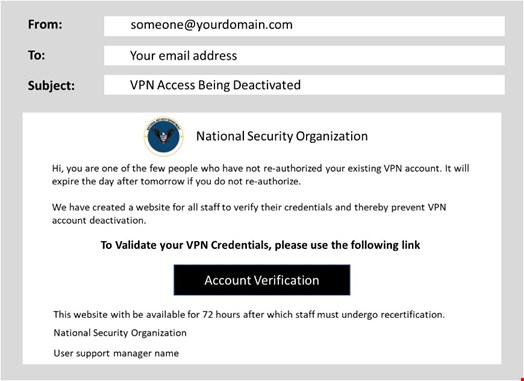
Just the other day, one of my colleagues at a federal agency reported receiving a message that looked like the featured image above. She clicked on the link, and fortunately, it was just a phishing simulation. She received warning messages from security, but later, at a virtual stand-up meeting, learned that everyone on her team did the same thing. Wouldn’t you? It’s the VPN. Your digital lifeline. To your paycheck.
Temporary Fixes
Like the phishing link clicker, technical teams at companies struggling to keep operating during the crisis all try to do what they think is necessary. IT staff and developers have had to rework many business processes and applications to operate entirely online.
For example, I bought a new USB headset from Best Buy. Picked it up at the curb, scant minutes after letting the convenient mobile app know I was there. That app, and many others, probably came from the cloud. Although in Best Buy’s case, perhaps a private cloud.
When they make quick fixes, technical teams tend to cut corners. They remove firewall rules that protect the perimeter. They increase administrative privilege levels or create new privileged accounts. They migrate to new cloud services from new suppliers.
Playing Catch Up
Many businesses, like Best Buy, or a financial services company I wrote about that had positioned itself a few years ago for a zero trust architecture, were already well prepared, but others were not. As of 2019, much of the business world had been actively discussing the “digital transformation” for well over five years. Gartner calls this trend digitalization.
According to Gartner surveys, more than 87% of senior business leaders say digitalization is a company priority, but Gartner cautions that only 40% of organizations have brought digital initiatives to scale.
Often, a cloud first strategy is the primary pillar of an organization’s digitalization strategy, but even businesses that claimed a cloud first strategy could dilly dally about fully building it out prior to this year.
If so, it’s time to play catch up. Architecturally, all the end users sent home from their private corporate networks are now “in” the cloud. Along with VPNs, the cloud has become our digital lifeline, and as the forced digitalization of COVID-19 continues, businesses are likely to move even more capabilities to the cloud.
Benefits and Challenges of Accelerated Cloud Adoption
The benefits of cloud include an expansion of solution choices and the outsourcing of some support functions. Without multi-cloud governance and cloud security architecture, risk and technical debt will increase in direct proportion the number of cloud service providers (CSPs), architectural pattern types, and integration or interconnection methods required to work with premise-based systems.
With some businesses even opting for a “cloud only” IT strategy, one might ask if there is even a need for an IT department. I think the answer is yes: Although cloud reduces support requirements, to manage hundreds or even just tens of cloud providers, business needs a shared pool of technical and architectural expertise to deliver on the promise of lowered costs and increased agility as well as to manage security and risk.
Develop a Cloud Security Strategy
Establish a cloud security working group to coordinate cloud efforts across IT, development, line of business organizations and corporate administration functions such as legal, HR and procurement. This group can help other IT teams drive their evolution from “IT-as-provider” to “IT-as-broker.”
The cloud working group must also develop tools and processes for identifying the risk of shadow IT, and by working with a third-party risk management team, ensure that useful CSP capabilities in the LOBs move into the IT (or security) service catalogs and that riskier CSP engagements require a higher bar for justification.
Bottom Line
The mix of an expanded cloud portfolio with the remaining premise-based IT systems and application footprint, when not governed and/or poorly integrated, creates issues with increased risk and technical debt that businesses must address through a cloud security strategy.
As you overcome the initial challenges of secure remote access, cloud adoption will bring the next wave of challenges. Don’t let your guard down!
