The increasingly mobilized world requires a new breed of information security techniques to strengthen the access to information systems. The contemporary initiatives in the industry such as PSD2 emphasizes the requirement for having strong authentication for information systems such as online banking, financial markets, health information systems, etc.
On the other hand, geo-location based adaptive authentication does not take into account the fact that user may change their login location periodically. However, we could leverage the rate at which login location changes as a mean of implementing an added layer of security for information systems.
What is geo-velocity based authentication?
Geo-velocity based authentication relates the login history of users with their login locations as criteria for granting access to the requested resource. For example, if user Alex logins to the system on a particular day at 3:00 pm (GMT) Monday from London, UK and then it is highly unlikely another login happens at 3:15 pm (GMT) Monday (on the same day) from New York, USA using the same user account.
Particularly for highly security sensitive systems such as credit card authorization, fund transfer systems, such a scenario could not happen at all’.
On the other hand, if there is another user login at 2:00am (GMT) on Tuesday on the same user account in Beijing, that can be allowed if there are possibilities of travelling from London to Beijing in the given time range.
Therefore, if we apply geo-velocity based filtering in the first case described above, it is impossible to travel from London to New York within five minutes, hence it should be blocked. However, the latter scenario could be allowed.
What benefits are provided by geo-velocity based authentication?
Geo-velocity based authentication is important for frequent long-distance travelers. The fact that the user travels frequently can be taken as a factor for authenticating them. This way geo-velocity based authentication opens-up a novel characteristic for an authentication factor of “where you are” in multi-factor authentication of authenticating the user by analyzing their login behavior along with the login location history.
How geo-velocity based authentication can be implemented?
Geo-velocity is naturally associated with people’s ability to move between different locations and how fast they could do that. The movements can be either domestic (e.g., fly between Seattle and Boston cities of USA) or international.
A pruning heuristic algorithm with two-levels of reasoning can be used for implementing the geo-velocity based authentication. Since the fastest available public transportation is a passenger jet which has average cruising speed of less than 1000 km/h, it can be used as a heuristic to filter authentication requests made from two geo-locations. Hence any velocity which is larger than 1000 km/h should immediately be rejected.
If the geo-velocity is below 1000 km/h we should check the other possibilities of travelling between the two locations. For example, the system should check the flights availability between the two locations.
What is the system architecture of a typical geo-velocity based authentication system?
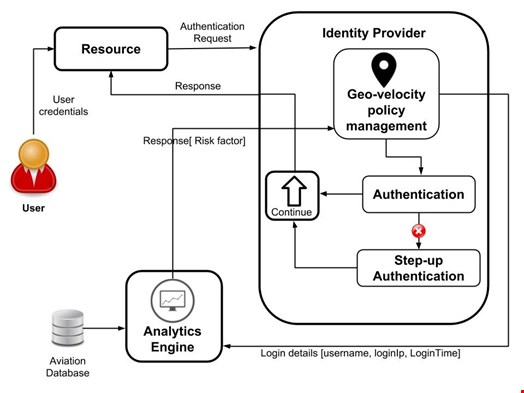
Geo-velocity based authentication can be developed as an integration between an identity and access management solution with an analytics engine (e.g., a stream processor) as shown below.
In nutshell, when the user tries to gain access to the resource by providing their user credentials, the request is sent to the identity server. An analytics engine authenticates the user based-on geo-velocity and user login details such as username, login time, and login IP are passed to the analytics engine.
Next, the analytics engine analyzes current login details with the previous login details, consulting an aviation database if necessary and defining a risk factor. Based on that risk score, the system decides whether to give the access to the resource or to step-up the authentication by authenticating the user with another strong authentication method.