In the course of the last five to seven years, advances in platforms like Skype, Google Hangouts and WhatsApp have made it easy to have meaningful face-to-face interactions across between two points anywhere on the globe.
Remote teams can conduct important meetings and grandmothers can tuck their grandkids in with a good night story despite time zones and distances, all thanks to the technologies that power these platforms. Yet while we enjoy the incredible convenience provided by video calling and conferencing technology, society hasn’t realized that they are yet another potential vulnerability to our privacy and security.
Hacking Video Calling and Conferencing Platforms
It might not come as too much of a surprise, but even these platforms can be hacked. In August 2018, Google Project Zero researcher, Natalie Silvanovich, disclosed that she had located critical vulnerabilities in most common video conferencing architecture implementations, including WebRTC (used by Chrome, Safari, Firefox, Facebook Messenger, Signal and others), PJSIP (used by WhatsApp) and Apple’s proprietary library for FaceTime. If exploited, such vulnerabilities would have let attackers crash apps using the implementation, by merely placing a video call. This would have then triggered a memory heap overflow which could allow the attacker to take over the victim’s video calling account.
An attack could be orchestrated in a couple different ways:
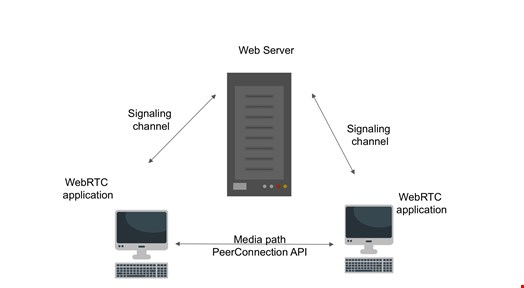
We’ll use WebRTC as an example. If we simplify the protocol to its basics, the consumer would use a signaling server to initiate communication and then communicate directly using the PeerConnection API. This is shown in the diagram below:
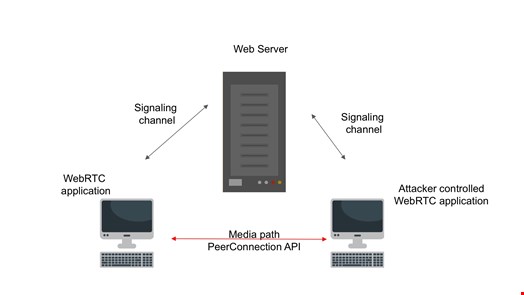
In an attack scenario, the invader implements a client, leveraging the found vulnerabilities, and then uses the existing signaling server to initiate communication and execute the attack, as depicted below:
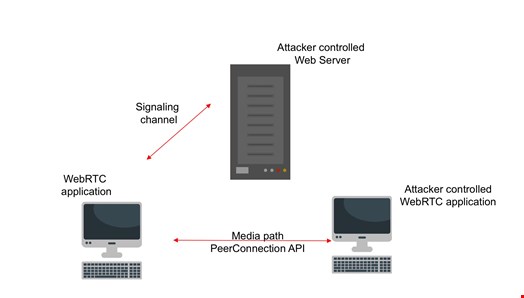
A more complex, but still possible option is where the attacker also takes over the signaling server. In that case, the attacker tries to persuade the target into connecting to a signaling server under their control (for example, by using the browser and convincing the target click a link). The attacker then uses that to trigger and exploit the found vulnerabilities. See below:
According to Silvanovich, these vulnerabilities are fairly serious. These libraries are used by many video conferencing platforms, including FaceTime and WhatsApp, and all of them could be vulnerable to such attacks.
Famed vulnerability researcher Tavis Ormandy backed Silvanovich up, and has been quoted saying “This is a big deal. Just answering a call from an attacker could completely compromise WhatsApp.”
Only a Proof of Concept — For Now
Scary, but as far as anyone knows, this exploit only exists as a proof of concept, which means that it has not been attempted by attackers. Shortly after the vulnerabilities were reported to WhatsApp and FaceTime, they were patched and are no longer considered to be a threat.
However, it does mean that attacks against video calling and conferencing platforms can, and most likely at some point, will be pulled off. Although the above vulnerabilities have been mitigated and attackers thankfully cannot use such means, it probably won’t be long before they find other ways to get what they want.
You might be wondering what attackers could possibly want when it comes to hijacking video calls. For consumer users, attackers may just be looking to take over WhatsApp, FaceTime and other accounts as another means of accessing their personal data.
For enterprises using conferencing platforms as a way of conducting meetings, attackers have the potential to eavesdrop on sensitive business conversations. This means that even if your corporate perimeter defenses are properly shored up, you could unknowingly be sharing the information they’re looking for, with every remote meeting.
How to Protect Yourself From Video Conferencing Vulnerabilities
There are ways that consumer and enterprises can ensure they don't become a victim when attackers do find new ways to exploit these platforms:
- Update to the latest version of the video platform as soon as an update becomes available. These updates contain patches to flaws when they are identified and any delay of these updates puts you at risk.
- Put your video conferencing platform behind a firewall. This will mitigate unauthorized access to your video conference infrastructure and restrict its access to other resources if compromised.
- Don't answer calls from unknown callers. Truthfully, this is just a smart piece of advice to heed in most situations. Attackers are crafty and you never know what method they might think up next, so it’s best to just ignore anyone suspicious.
As with all proof of concepts, now that the cat is out of the bag, we can (and should) expect attackers to turn their attention to this vector. This is a frightening prospect, but on a more hopeful note, perhaps these disclosures will encourage the developers of video conferencing platforms to conduct better vulnerability testing in pre-release stages. Let’s hope that better security measures will be built-in so that when attackers do test the waters, they’ll be unsuccessful.
