Secure cloud data processing has become a critical issue in recent times and while general network security techniques such as Virtual Private Networks could be used for securing the end-to-end communication of a hybrid cloud. However if the cloud computing platform has been compromised, then the data will be at risk despite the end-to-end encryption, so one solution could be Fully Homomorphic Encryption (FHE or simply Homomorphic Encryption).
This is a form of encryption which allows arbitrary computation on encrypted data (i.e., cipher texts) and generates an encrypted result which when decrypted, matches with the results of the operations performed on the original data that have been performed on the plaintext. This allows for data to be hidden from the processor since it is not required to decrypt cipher texts at the public cloud level.
What are the benefits of elastic stream processing?
Stream Processors are software platforms which allow users to respond to incoming data streams faster. We apply homomorphic encryption on top of Elastic Stream Processing; a data analytics technique which provides load balancing of data stream processors with clouds.
When there is excessive load on the stream processor located in a private cluster, more compute resources can be provisioned from public cloud and part of the workload can be delegated to the public cloud. This allows for maintaining the agreed upon service quality attributes. Elastic Switching Mechanism (ESM) is an example for such load balancer.
How can homomorphic encryption for stream processing be implemented?
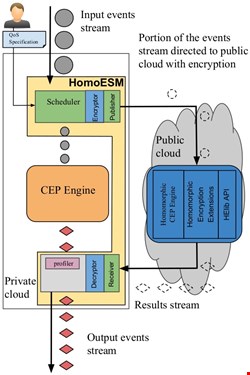
The image below shows a possible approach for implementing homomorphic encryption based elastic stream processor (HomoESM). Part of the input stream is sent to the public cloud by encrypting it with homomorphic encryption using HElib API. The portion of the data stream processed within the private cloud is sent to the Complex Event Processing (CEP) engine which gets processed directly.
A homomorphic CEP engine that is running on public cloud processes the encrypted stream. The processed results from the public cloud is decrypted and merged with the event stream output from the CEP engine.
What are the important points to note?
There are multiple approaches for implementing homomorphic encryption. Some of them are purely CPU based (e.g., HElib) while others use both CPU and GPU (Graphical Processing Unit) (e.g., CuHE). However, the approach to be used really depends on the use case: use of GPUs enables the encryption and decryption tasks to work faster, which is essential for achieving low latencies.
However, in the case of network intensive applications such as elastic data stream processing the message size also should be taken into consideration. If the GPU based encryption produces lengthy messages compared to the CPU based approach, then the CPU based technique should be utilized to implement the application.
In addition, HomoESM uses an event stream compression technique called “Composite Event” creation which aggregates the fields of the events of the event stream into batches. This technique allows for more events to be sent to the public cloud and get them processed much faster by reducing the message sizes sent to the public cloud.
To what extent can this be practical?
Capabilities of homomorphic encryption has been improving over the years. However, the current systems are operating within application specific constraints. The HomoESM described above supports addition and subtraction homomorphic encryption operations in a message range of 0 to 1201. Therefore, it is required to know the range of possible data values which can be present in a data stream in order to apply FHE for that particular use case.
Use of 32-bit full adder circuits using HElib could increase the range further. If such limitations could be mitigated a system like HomoESM, it could produce up to 26% performance improvement with elastic scaling.
Traditionally homomorphic encryption is known to be computationally expensive operation but with optimization it can be done based on the use case to mitigate the drawbacks of homomorphic encryption.
For example, data batching and asynchronous event publishing could be used for obtaining performance improvements. HomoESM is an example system for use case specific tuning of homomorphic encryption for obtaining secure outsourcing of workload to public clouds.
