Organizations are relying more than ever on technology and information processes and systems to deliver critical operations. Given this operating environment, the occurrence of incidents resulting in degradation of key systems or disruptions to an organizations’ critical operations is inevitable.
Organizations cannot predict or control when an incident will occur but can control their ability to detect, respond and recover, thereby minimizing the severity of the impact.
This article aims to increase the awareness of the incident management process and its importance. This includes describing a commonly used approach to incident management and pitfalls to address in maintaining an effective incident management program.
Incident management involves a series of structured processes and practices to identify potential disruptions, develop response plans and respond effectively to incidents that disrupt operations or pose security risks.
Organizations need to prioritize the development and implementation of such a program to be resilient. This will enable organizations to swiftly address and minimize disruptions, protect sensitive data, maintain stakeholder confidence and build resilience against future cyber threats.
Understanding Incident Management
The goal of incident management is to minimize the impact of incidents, restore normal operations as quickly as possible and learn from the incidents to improve future responses.
The National Institute of Systems and Technology (NIST) Special Publication 800-61 defines incident management as the process of detecting, responding to, and recovering from security incidents.
NIST provides a structured approach to managing incidents to minimize their impact on business operations and ensure a swift return to normalcy. This approach has four phases as captured below in the incident response life cycle.
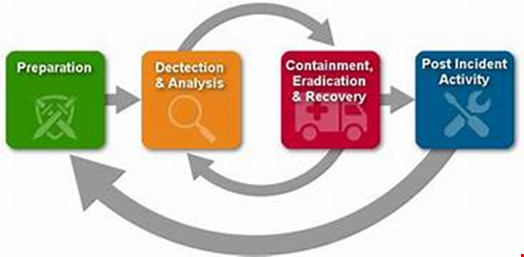
- Preparation: This includes not only developing incident response capability but also preventing incidents by ensuring that systems, networks, and applications are sufficiently secure. Also, creating policies, procedures and response plans, as well as training the incident response team.
- Detection and Analysis: Continuously monitoring systems and networks to detect potential incidents and analyzing the data to assess their severity and impact.
- Containment, Eradication, and Recovery: Taking immediate actions to contain the incident, remove its cause, and restore affected systems to normal operation as soon as possible and securely.
- Post-Incident Activity: Reviewing the incident and response efforts to identify lessons learned and areas for improvement. This phase also involves updating incident response plans and procedures based on the lessons learned and insights gained.
Common Pitfalls in Incident Management
Organizations should recognize and address common pitfalls that can undermine the effectiveness of their incident management program.
These pitfalls include the failure to continuously update the incident response plans, a lack of regular testing of these plans, and the absence of ongoing improvement efforts based on lessons learned.
Failing to Revise the Plans for Changes
A common pitfall in incident management is failing to regularly update the incident response plans. It is essential that the plans remain current and considers personnel changes, new technology applications, or modifications in hardware and software.
Also, for a plan to be effective, it must have a clear definition of who is responsible for these updates and the frequency of the updates. Without regular updates, plans can become outdated and ineffective, leaving the organization vulnerable to new and emerging threats.
Regular reviews and updates ensure that the incident response strategy remains relevant and capable of addressing risks.
Lack of Regular Testing
Another pitfall is the lack of regular testing of incident response plans. Without regular testing, organizations may not be aware of the gaps in their plans until an incident takes place. Also, testing allows individuals to practice their roles and responsibilities and the actions to take and refine the plans.
Inadequate Process to Identity and Incorporate Lessons Leaned
The absence of continuous improvement efforts, a process to learn from incidents and enhance response plans going forward is also a common pitfall in incident management program. Continuous improvement involves post-incident reviews, incorporating lessons learned and ultimately leading to a more robust and effective incident management plan.
Conclusion
In today's rapidly evolving digital landscape and stakeholder expectations, effective incident management is crucial for achieving resiliency, protecting sensitive information and maintaining stakeholder trust. By understanding the importance of incident management and its goal of minimizing the impact of incidents, organizations can proactively prepare for and swiftly respond to disruptions.
However, common pitfalls such as not regularly updating the recovery plans for changes, inadequate testing and not incorporating lessons learned from incidents can undermine the effectiveness of incident management program.
It is critical for organizations to prioritize incident management and create a proactive and resilient security culture that can withstand and adapt to the ever-changing threat landscape to maintain operations.