In January, the NSA issued guidance titled: “Mitigating Cloud Vulnerabilities.” With security organizations already overburdened with too many threat intelligences feeds, alerts, mandates and fire drills, it’s understandable that this information might go unnoticed, or be tossed onto the “we’ll get to it sooner or later” pile.
However when an organization like the NSA speaks, it is generally a good idea to listen. Which raises the question: how does one operationalize guidance from the NSA and other elite security organizations? The short answer is the same as it is for all cybersecurity undertakings: prioritization and outcomes. Let’s examine this approach, using the recent NSA guidance as our use case.
Vulnerability Components
The NSA broke down its guidance into four key vulnerabilities: misconfigurations, poor access control, shared tenancy vulnerabilities and supply chain vulnerabilities. It also provided this handy chart to articulate the prevalence and sophistication of exploit for each.
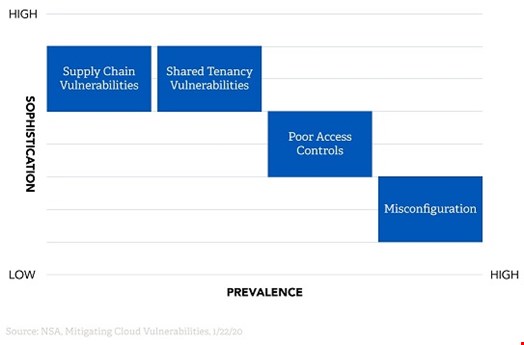
This chart provides clear prioritization for security professionals. In a time where resources (particularly skills on staff) are strained, it is critical to attack problems that represent the highest risk. Here is a look at each.
Misconfigurations
If we’ve learned nothing else about threat actors over the years, it’s that they want a good return on investment. This means they’ll take the easiest route to stealing data, every time. It is for this reason that misconfigurations represent such a risk to enterprises – there is nothing easier than stealing data left exposed by bad configuration management.
Cloud configuration management poses a particularly vexing problem because with the advent of DevOps, the cloud environment is constantly changing. This makes cloud monitoring a major challenge and, within that discipline, configuration and policy management need to transition to a continuous state. Here are the key elements of a modern cloud monitoring program:
- Cut Through the Haze: First, gain visibility into the cloud to effectively track disk configurations, mislabeled tags, CIS benchmarks, regulatory modules, NIST frameworks, etc. Many cloud providers offer strong monitoring tools within their platforms, and there are many third-party tools as well.
- Automate Remediation: There is no way to manually keep pace with all the changes in the cloud, so it is an ideal case for automation. IT teams can do this by creating functions with logic written around them. For example, “if there is a cloud storage that has a public read attribute to it, then shut it off or encrypt every object that gets uploaded.”
- Update Processes: Processes must evolve to accommodate automation. Many enterprises move from on-premise to the cloud while retaining legacy change-management processes, which are often at odds with automation, so they need to be modernized.
Creating a continuous cloud monitoring program is the most important thing enterprises can do to operationalize the NSA guidance. Now let’s look at the next most important thing.
Cloud Access Control
Exploiting poor access control in cloud systems takes a higher degree of sophistication than simply looking for exposed data, so it is not yet a major contributor to cloud data breaches. However, the problem is widespread and stands to become such a contributor, if organizations do not improve their identity and access control processes.
The good news is – the first step to ensuring strong access control in the cloud is also the first step to achieving continuous cloud monitoring – visibility. Because cloud services and systems can be spun up by virtually anyone in an organization, it is critical to have the visibility required to understand when this is happening, so security pros can ensure proper access control.
The recurring theme in the NSA guidance is multifactor authentication. Enterprises can dramatically improve the integrity of cloud access control if they implement multifactor authentication across all cloud resources. Ideally, this will be part of a broader enterprise identity and access management (IAM) program that brings all enterprise resources – on premises, in the cloud, and hybrid – under appropriate identity governance.
Shared Tenancy and Supply Chain
I’m lumping these together because, for the most part, they are primarily the responsibility of cloud service providers, not the enterprise, and exploitation requires a high degree of sophistication. Therefore, as we sit here today, they are not a likely source of risk. The compromised hypervisor has been a nightmare scenario since the dawn of server virtualization, but according to the NSA, there have been no reported isolation compromises on major cloud platforms (although researchers have demonstrated the possibility of container of hypervisor compromises).
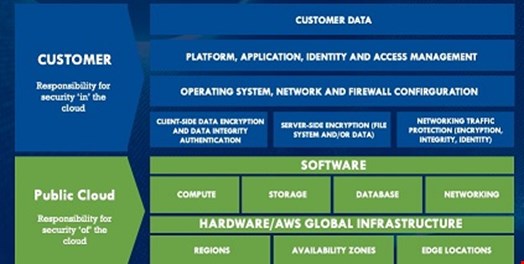
As for supply chain issues, that is the domain of cloud service providers (see chart below). They must do proper due diligence and continuous monitoring to ensure that none of their software or hardware components are vulnerable.
If nothing else, remember the two words that should define cybersecurity strategy and operationalization: prioritization and outcomes. If all security organizations prioritized activities based on the reduction of business risk (the desired outcome), the cyberworld would be a much safer, simpler place.