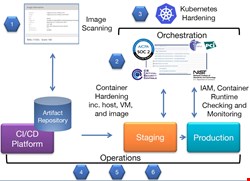
There are lots of potential benefits to adopting container technology like Docker. It allows you to move swiftly, enabling scalable deployments which can be largely automated.
Docker makes it easier to introduce agile and lean processes into development, testing and security operations. There’s a great deal of transparency to the code and images, it’s consistent and predictable, and it reduces your potential attack surface.
Little wonder, then, that Docker adoption grew 40% in the last year, according to Data Dog, or that larger companies are leading the way, with 60% of organizations running 500 or more hosts classified as Docker dabblers or adopters.
Docker’s popularity is partly because it’s designed to be secure, but there are issues you should be aware of. It pays to plan a proper security strategy for your Docker containers by starting with a clean image, hardening the host OS, restricting user access and monitoring container operations.
Developers often download public images from unknown open-source sites and there’s an element of risk involved here. Consider that 24% of the latest Docker images have significant vulnerabilities, according to Federacy. That’s based on scans of official Docker repositories. Wherever you pull images from, you really need to integrate image scanning into your process.
While the container attack surface is minimal, the challenge is that all containers share the host operating system, so there’s a chance of interference because of misconfiguration or misbehaving containers that could affect the entire operation. Since they share the host operating system or a virtual machine environment, depending on your deployment scenario, they may be vulnerable to host-level security risks. There is a need to ensure that they are hardened. Remove unnecessary software packages and services, restrict access and set up intrusion detection.
Docker adopters nearly quintuple the average number of running containers they have in production within ten months, according to Data Dog, 40% use orchestrators to effectively manage and orchestrate their containers.
When managing a cluster of Docker machines, there’s a tangible need for a streamlined process to ensure that all this orchestration is secure and managed properly. Network segmentation is recommended to isolate clusters of hosts or machines that need to communicate for a particular service function that the developer is trying to achieve. If you employ Kubernetes, then make sure you’re up to date with the latest security benchmark.
There should be a centralized approach to decide how privileges are assigned and managed in an enterprise friendly manner. User authentication and authorization is key and must reflect behaviors and permissions to enforce strong separations of duty and access controls. Having a role-based access control mechanism, that ties into the enterprise identity and access management framework, is vital for implementation.
It’s crucial to ensure that structured images are used in the processes, whether it's a private container or a public container. There should be minimal image clutter. Make sure that all images are signed before they get used in the development cycle. Having various gates during the development process, the build process and the testing process to ensure that these policies are enforced and managed properly is vital. On top of that, you need a tool to manage privileges, passwords, and tokens so that the right people have access to the right images.
Once your container is deployed, there's a need to monitor the container operations. Make sure that any erroneous behavior is detected. If there is some anomalous behavior, such as outbound network connections that are deriving from the container, it needs to be observed, logged and dealt with in a timely manner. You should aim to continuously improve the system through discovery, assessment and remediation. Effective ongoing monitoring is essential to make that possible.
These are just a few things to consider when securing Docker containers. For a more comprehensive overview it’s a good idea to refer to NIST’s Application Container Security Guide. You can also work towards security and compliance standards via a range of frameworks and benchmarks available at the Docker website.