5G telecommunications and its associated infrastructure will leverage highly distributed, virtualized and software-defined networks. This approach will improve service delivery, reduce backbone maintenance and hardware configuration costs, and provide more remote control for network operators. However, due to the increased connectivity 5G will introduce combined with the amplified virtualization across the telecom backend, new risks around DDoS attacks are emerging.
One key area of growth that will drive demand for 5G services will be the dramatic increase in Internet of Things (IoT) device usage. Network services will need to be provisioned at greater levels of reliability, maintainability and speed that private and public carriers are currently unable to provide. Telecom companies aim to overcome some of these limitations with the deployment of fifth generation communication systems.
Many of new IoT connections will be generated from industrial robots, factory vehicles, predictive maintenance sensors for infrastructure in smart cities, connected tools, wearable technology, telemedicine and remote surgery appliances. Latency, throughput, and reliability demands of these devices will vary. Therefore, providing a one-size-fit-all 5G service offering would be fiscally unsustainable and unnecessarily burdensome on core network resources. Instead, telecom providers are leveraging virtual architectures implemented as network slices to customize service deliveries for different types of applications and enterprise service models.
Network slicing enabled by Network Function Virtualization (NFV) and Software-Defined Networking (SDN) technologies will be a key technical driver behind 5G deployments. It will allow carriers to provide new services with increased flexibility at lower CAPEX and OPEX.
NFV and SDN: Separating Control and Data Planes
From a technical perspective, NFV means that network services, such as routers, firewalls, load balancers, XML processing and WAN optimization devices can shift from being run on dedicated single-function hardware, to instead, being configured in software running on virtual machines. Under the control of a hypervisor, these technologies allow several applications and operating systems (OS) to run on a single physical server.
SDN refers to the high-level, centralized control over a virtualized environment, where logical intelligence of network functions is split from the hardware-based packet engine. This can be described as a separation of the network control and data planes. SDN tools control where traffic will be sent to, while a combination of virtualized devices and traditional hardware continues to direct data packets and handle the actual traffic load. By applying programming and automation to network control, operators can define, manage and manipulate logical networks directly and dynamically without needing to install new or swap out older and narrowly focused devices.
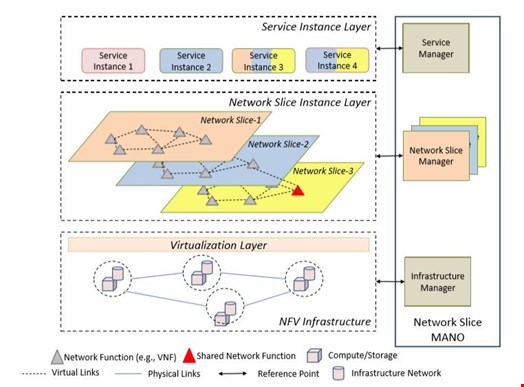
Different customer requirements will be solidified in enterprise service-level agreements (SLAs) across this shared environment, specifying bandwidth, mobility, resiliency, security, and availability. A Network Slice Management and Orchestration (MANO) architecture overview can be seen in Figure 1 below, with each slice representing an independent end-to-end logical network.
DDoS Risks
In a traditional telecom environment, many physical devices or appliances are dedicated to primarily one task. These devices often have application-specific integrated circuits (ASICs) that can be tailored to meet the exact requirement for the product using the circuit, such as a switch, router or firewall. Additional physical components are not necessarily required for the product to complete its primary function and processes. ASICs are very stable and are built to manage peaks and increases in network traffic or applying access control lists on a firewall, for example. This provides a strong resistance to Denial of Service (DoS or DDoS) attacks. However, NFV moves network functionality away from physical appliances and runs them in software on CPUs. This software is significantly more vulnerable to being disrupted by targeted traffic increases—such as the high volume loads that exist in a DoS attack.
5G-enabled devices can also deliver more compute power and speed, which means that DDoS attacks won’t necessarily need to control as many endpoints in their botnets. This will likely lead to larger volumetric attacks, which have already exceeded multiple terabits per second. Ultimately, SDN and NFV will be key enablers of 5G’s highly distributed and virtual architectures at scale, allowing different industries with different network requirements to receive affordable and tailored service offerings. While the business case is clear, carriers and customers must understand that these architectures will expand the attack surface and create new challenges for managing DDoS risk.
