Since they’ve existed, web applications have been a favorite target for hackers. They are relatively easy to break and give hackers potential access to sensitive information, as well as serving as an entry point to an otherwise well-protected system.
Last year, an investigation into data breaches by Verizon found that web applications are among the top three attack vectors across eight of the nine industry verticals studied. Moreover, web applications took the leading spot in four of those vertical sectors.
Why is Key Protection Needed
Information shared via a browser needs to be encrypted to ensure it cannot be improperly accessed by individuals intent on exploiting it, and while cryptography may be thought to be fully secure, in reality, it simply shifts the problem from protecting the data to protecting the keys that encrypt the data.
In short, encryption is only secure if the keys used for the encryption are kept secure. If those keys are easily accessible, then so is the encrypted data itself. In fact, hackers use a variety of techniques to try to extract these keys, including: reverse engineering, untangling software programs to discover how they work, or examining code to find hard-coded keys and then using those same keys in attacks against the server, are among common methods.
Attackers are also adept at scanning memory during an app’s runtime to reveal the cryptographic keys that are used in encryption operations. Side-channel attacks that attempt to find keys by exploiting indirect information like patterns of memory access are also a part of their malicious offensive.
Once they’ve been snagged, cryptographic keys can be used for a wide range of subsequent attacks both on the client-side system, or the server that uses the keys. The keys are like gold for rogue actors who profit from breaking through defenses to access and exfiltrate sensitive data, spoof an authentic user identity, or even snoop on secure communications.
Hackers have also been known to use keys to generate fraudulent digital signatures which mimic ‘trusted’ protections and are used for further attacks. A well-armored cyber-criminal can also create, modify or even delete data or transactions, causing untold damage to systems with unreadable commands, and to individuals and organizations whose sensitive information is lost or altered.
The Challenge of Storing Keys
One of the major challenges of using cryptography to protect data in web applications is the question of where to securely store cryptographic keys on the client-side. Secure elements, trusted execution environments and hardware security modules are strong solutions for cryptography key storage, but often web applications do not have access to these technologies.
The ease-of-use and reliability of web browsers as an application platform have been the primary drivers behind the huge surge in web application popularity. However, while convenient, the browser environment poses enormous security challenges. For example, private cryptography keys on the client-side often represent the actual identity of the user. Safeguarding these keys and preventing their disclosure to anyone, irrespective of intent, is critical.
Unfortunately, the usual solutions for keeping cryptographic keys safe on devices and PCs are not applicable. This is because browsers do not have access to underlying hardware security support. As a result, one of the most crucial elements of cybersecurity infrastructure is also one of the most vulnerable.
Existing Options are not Enough
Storing cryptographic keys in the browser has been an ongoing challenge and several attempts have been made to introduce a solution that is easy yet secure. Perhaps the most popular, Web Crypto API provides cryptographic algorithms, and is arguably better than ‘build-it-yourself’ defenses because it is hard to get these algorithms right.
In addition, Web CryptoAPI is built into the browser which is an advantage because hackers cannot attack it directly from a web app. Instead, they must have some kind of access to the browser executable, or the underlying platform.
However, key management and storage is notoriously difficult. The Web Crypto API provides some limited key management features including key generation, key derivation, and the ability to import and export keys, but it does not directly support any key-storage mechanism.
IndexedDB API or Web Storage API are the recommended key storage mechanism, yet neither of these technologies provides access to secure hardware-based key storage. This opens up a key-lifting vulnerability via reverse engineering, memory examination, or side-channel attacks.
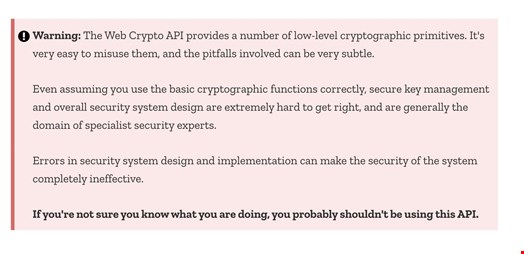
Solutions like Web Crypto API are also complicated to set up and use, a source of frustration and limitations to many users. Below is a screenshot from the Mozilla Developer Network highlighting caution in using the Web Crypto API.
A Solution that Works
White-box cryptography is a solution that provides software-based key storage. It is highly resistant to reverse engineering, memory examination, and side-channel attacks. Fundamentally, it is an obfuscation technique that is intentionally difficult to reverse engineer, and the keys are not stored in the code in any simple way. Essentially, keys are embedded in the algorithms making it inherently hard to extract them.
Similarly, the keys in a white-box implementation are never exposed even in memory, meaning memory examination techniques will fail as well. Finally, modern white-box cryptography implementations have been engineered to be side-channel attack resistant.
This makes white-box cryptography a particularly viable solution for dealing with the types of web app vulnerabilities that arise from the limitations of key management and storage offered in common cryptographic libraries. It ensures sensitive keys are always encoded and difficult to extract and tamper.
