| Title: Easy Password Creation Systems for Life |
| Author: Josephine Rosenburgh |
| Publisher: e-book, available at smashwords.com |
| Price: $5.50 |
Advice on creating a password is plentiful. Just read the comment section of any popular article or blog post about passwords and you’ll see people pitching their particular password generation scheme. What you see less frequently is careful analysis of how well these techniques actually stand up to both user acceptance and attacks.
The e-book Easy Password Creation Systems for Life by Josephine Rosenburgh aims to help generate stronger random-looking passwords without forcing users to commit the whole thing to memory.
Rosenburgh’s technique creates a 20-character password using a premade grid of characters. Because password strength tends to quickly grow with password length, this is a good ambition. Unfortunately, not all websites or systems allow passwords of 20 characters, so users will occasionally be forced to shorten it.
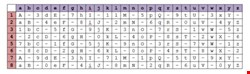
The grid is arranged with the letters A to Z as the 26 column labels and the numbers 1 to 8 as the eight row labels. This forms 208 grid squares, each containing one of 63 unique characters, made up of a pattern of lowercase letters, uppercase letters, numbers, and the hyphen symbol (see Basic Grid image). A hyphen was chosen by the author because she felt it was a commonly accepted symbol for passwords, but this too will depend on the particular rules of a site’s password policy.
Because the characters in the grid follow a pattern, a user could try to memorize the layout to recreate it as needed. The author, however, admits that most people will need to carry a copy of the grid around with them. A printout of the grid becomes a ‘what you have’ authentication factor rather than a ‘what you know’ factor, saving users the need to commit more to memory.
Armed with the grid, a user’s first job is to create a five-character personal code consisting of a word or letters. This personal code is used in the construction of all passwords – a master password of sorts. A user then must also randomly select three numbers between 1 and 8. These numbers are combined with the letters of the personal code to form grid coordinates.
For example, with a personal code of ‘TOWEL’ and the numbers 2, 5, and 8, the first characters of the password would be the value of grid squares T,2 followed by O,5 then W,8 and so on, repeating the number sequence as necessary. This generates the five character string ‘0O-e-.’
The next step is to create a four-character site code. So if a user was logging into Infosecurity magazine’s website, they might use ‘INSM’. A different site would have a different site code. The user then follows the same process of combining those letters with their random numbers to get the coordinate of their next password character. Using ‘INSM’ we add the characters ‘in-m’ to our password.
Regrettably, coming up with the final eleven password characters is less straightforward. In the book example, Rosenburgh randomly chooses a few sets of coordinates to pad out the remainder of the password. She briefly mentions the alternatives of reversing the site code or using other portions of the site name for the final coordinates. There is very little discussion of good and bad approaches for doing this. Essentially this means that after the formulaic first half of the password, the second half is left to the user to figure out.
This is one major concern about the book’s proposed technique. The average user needs fairly specific instructions on how to create a password that avoids the typical security pitfalls. You couldn’t hand this book to several different people and count on them all coming away with a consistent password creation process.
Variations of this grid system have been used for password creation in the past, and generally they rely on the user to memorize either a single keyword or a grid start and end point. If a user has to remember more pieces of information (a personal code, site code, random numbers, and a custom formula for the second password half) this makes it more likely that they will forget something.
Rosenburgh’s technique seems to increase both the memory burden on users as well as complexity of the steps needed to recreate passwords using the grid. If users must write down all these details, then they are probably better off generating a truly random password and writing that down (using a password manager) instead.
The author’s bio describes her as a fan of Sudoku and crosswords, which seem to serve as inspiration for her password creation technique. Unfortunately, the needs of people who want to spend leisure time on puzzles are not the same as those who just want to securely authenticate to computer systems. Due to this mismatch I feel the book fails to deliver on its promise of “easy” password creation.
This book was reviewed by Bruce K. Marshall, researcher & consultant, PasswordResearch.com